首页 > 代码库 > 实现基于SSL的FTPS
实现基于SSL的FTPS
实现基于SSL的FTPS
目 录
1、查看当前vsftpd是否具有ssl模块
2、创建自签名证书
3、查看证书
4、配置vsftp支持ssl
5、测试、利用filezilla 登录测试
6、wireshark抓包结果
Vsfptd普通数据传输十分不安全,例如用户密码等很容易被窃取
1、查看当前vsftpd是否具有ssl模块
[root@localhost ~]# ldd $(which vsftpd) |grep ssl
libssl.so.10 => /usr/lib64/libssl.so.10 (0x00007f55009bf000)
2、创建自签名证书
[root@localhost ~]# cd /etc/pki/tls/certs/ [root@localhost certs]# make vsftpd.pem [root@localhost certs]# make vsftpd.pem umask 77 ; PEM1=`/bin/mktemp /tmp/openssl.XXXXXX` ; PEM2=`/bin/mktemp /tmp/openssl.XXXXXX` ; /usr/bin/openssl req -utf8 -newkey rsa:2048 -keyout $PEM1 -nodes -x509 -days 365 \ -out $PEM2 -set_serial 0 ; cat $PEM1 > vsftpd.pem ; echo "" >> vsftpd.pem ; cat $PEM2 >> vsftpd.pem ; rm -f $PEM1 $PEM2 Generating a 2048 bit RSA private key ..................................................+++ ............................+++ writing new private key to ‘/tmp/openssl.x3aynR‘ ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.‘, the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:beijing Locality Name (eg, city) [Default City]:beijing Organization Name (eg, company) [Default Company Ltd]:mage Organizational Unit Name (eg, section) []:ftp Common Name (eg, your name or your server‘s hostname) []:172.16.250.90 Email Address []:ftp@mage.com
3、查看证书
[root@localhost certs]# openssl x509 -in vsftpd.pem -noout -text Certificate: Data: Version: 3 (0x2) Serial Number: 0 (0x0) Signature Algorithm: sha1WithRSAEncryption Issuer: C=CN, ST=beijing, L=beijing, O=mage, OU=ftp, CN=172.16.250.90/emailAddress=ftp@mage.com Validity Not Before: Dec 20 15:44:44 2016 GMT Not After : Dec 20 15:44:44 2017 GMT Subject: C=CN, ST=beijing, L=beijing, O=mage, OU=ftp, CN=172.16.250.90/emailAddress=ftp@mage.com Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:e4:7c:a3:98:d5:b6:a0:6c:3e:67:86:b0:98:79: ec:3d:d2:6a:76:bf:43:2f:8f:f9:bd:29:c2:11:50: 7a:64:24:b6:bc:64:9b:53:62:e2:25:44:7f:f4:ef: ea:81:01:92:ae:3a:02:f9:0a:75:92:00:62:97:64: a9:1e:d8:c0:89:4b:e0:1c:84:ea:d1:49:9b:80:97: a8:42:8d:00:ae:41:91:f7:3b:7e:19:58:32:57:2e: 6f:b3:e4:84:59:cc:4e:fe:04:6e:76:a2:6f:8b:ac: 5e:6c:98:28:1d:28:cb:d7:7f:df:e0:9c:85:eb:93: bf:c3:d7:8e:35:80:03:bf:8e:19:92:dd:4b:39:c3: 68:27:d2:4a:5e:b4:18:5d:02:08:2a:ce:66:00:64: 25:83:5b:dc:aa:9c:da:b2:5f:2e:59:bb:b7:eb:f0: 2c:e2:63:a4:f8:e0:2e:38:d8:ad:ba:0e:05:96:e5: 91:26:87:a6:a0:64:c5:bd:b0:ad:00:4e:b0:be:e2: 91:35:f2:36:5b:b3:56:f7:0a:fa:3d:e9:f9:4f:6b: ab:c0:2b:2a:a4:0b:d7:f7:5b:06:86:c1:85:59:b8: 6a:78:1b:55:05:e9:5c:51:dd:d3:0e:1a:75:0e:f1: 3a:b3:42:e6:62:02:d4:8b:30:fb:36:ec:75:5a:6d: 43:89 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Subject Key Identifier: C6:F8:38:E5:9A:17:9B:0E:D8:31:BE:DE:4E:29:14:DD:7F: EF:FB:FE X509v3 Authority Key Identifier: keyid:C6:F8:38:E5:9A:17:9B:0E:D8:31:BE:DE:4E:29:14: DD:7F:EF:FB:FE X509v3 Basic Constraints: CA:TRUE Signature Algorithm: sha1WithRSAEncryption dd:5f:de:d3:ff:53:ba:3a:69:7c:46:78:38:b1:07:b6:cd:5a: 5d:aa:fc:fb:4d:19:63:a9:06:1e:95:8c:56:2f:c5:1f:3c:7e: b2:6d:9c:7e:ec:c6:ba:60:6c:25:b5:35:6a:87:32:06:0c:37: 89:f1:b1:c2:bd:4a:17:91:2a:a7:5f:f9:56:eb:64:a5:b1:1c: b1:db:f2:dc:eb:60:fc:37:4c:ca:c2:68:9b:f5:36:77:d4:36: 43:e8:4b:54:48:72:f8:dc:fe:80:96:c0:6a:1d:2a:95:5a:f9: 47:2e:14:1f:7a:ba:db:d2:5b:5c:6e:d6:4b:d1:f9:1b:4d:26: a2:47:69:14:23:52:f5:13:d7:2f:57:f2:d4:be:77:c8:b0:c5: 4f:04:43:66:5e:fe:8e:2f:5b:e7:8b:f3:6b:b1:13:a1:cd:95: 90:f5:94:2f:b6:75:0d:67:45:58:36:d8:82:7d:ac:fd:79:2c: 28:24:d9:a2:98:02:30:31:8a:91:a5:c6:15:49:c6:91:19:ae: 90:5a:fb:57:ff:c7:36:27:5b:29:e1:79:ea:7b:33:68:2b:1a: e7:89:0e:96:7d:ac:eb:d3:81:d6:5f:35:ca:bb:3d:cf:1e:f7: 87:28:00:c8:c9:ff:9e:50:ca:aa:13:66:29:be:2c:f1:11:28: 02:19:b3:ca
4、配置vsftp支持ssl
anonymous_enable=NO #禁止匿名用户登录 chroot_local_user=YES #禁锢所用系统用户在家目录中 ssl_enable=YES #启用ssl allow_anon_ssl=NO #匿名不支持SSL force_local_logins_ssl=YES #本地用户登录加密 force_local_data_ssl=YES #本地数据传输加密 rsa_cert_file=/etc/pki/tls/certs/vsftpd.pem #证书 [root@localhost ~]# useradd -s /sbin/nologin wang 创建测试用户 [root@localhost ~]# passwd wang
5、测试、利用filezilla 登录测试
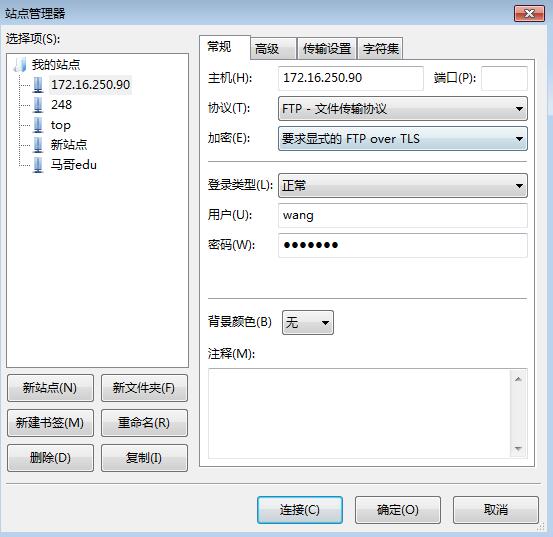
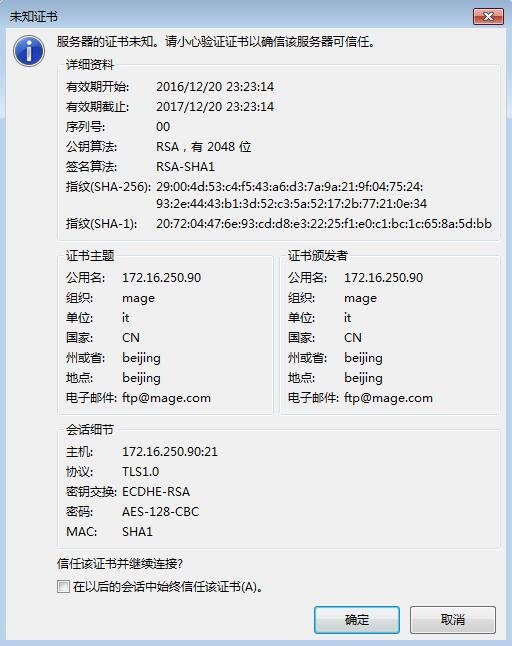
6、wireshark抓包结果

本文出自 “秋季” 博客,请务必保留此出处http://lxlxlx.blog.51cto.com/3363989/1885416
实现基于SSL的FTPS
声明:以上内容来自用户投稿及互联网公开渠道收集整理发布,本网站不拥有所有权,未作人工编辑处理,也不承担相关法律责任,若内容有误或涉及侵权可进行投诉: 投诉/举报 工作人员会在5个工作日内联系你,一经查实,本站将立刻删除涉嫌侵权内容。
