首页 > 代码库 > 马哥第六次作业
马哥第六次作业
1、详细描述一次加密通讯的过程,结合图示最佳。
答:
单向加密解密过程:
发送方:
1)发送方用对称加密的方法提取文件的特征码,用自己的私钥加密这段特征码,并附加在文件后面(还是明文的);
2)用一个对称密钥,借助于对称加密算法把整个文件加密;
3)再用对方的公钥加密对称密钥,附加在文件后面;
接收方:
1)接收方先用自己的私钥解密出对称密钥;(能解密说明的确是用自己的公钥加密的;)
2)把解密出来的密码,借助于解密算法,就能解密出文件数据;
3)得到文件的明文数据和加密的特征码;
4)用发送方的公钥去解密特征码;(能解密说明对方的身份得到认证)
5)再用同样的加密算法计算文件数据的特征码;比较两个特征码是否一样;如果是一样的说明文件的数据完整性得到认证;
例如两者A,B进行加密通信:
双方建立TCP连接,B将自己的CA证书用经过私钥加密后发送给A,A使用存留本机的CA证书库中找到其公钥进行解密,如果能解密说明证书可信任,下一步比对其主机名,如果主机名正确可以进行交换,下一步使用单向加密,加密其特征码与证书中的特征码进行比对,如果正则,则保证了证书的完整性,下一步进行数据交换!
A将发送的内容进行编写而后发送给B;
使用单向加密算法提取数据的特征码,用自己的私钥加密这段特征码附加在这段数据后面
A再用对称密钥将这整段数据进行加密,此时B是没有这段对称加密的密钥的,那么可以使用B的公钥加密这段对称密钥附加在上一段数据后面。
B使用自己的私钥解密对称加密得到对称加密密钥,使用对称解密算法得到明文数据和特征码,使用对方的公钥解密特征码,使用同样的算法提取特征码,说明数据完整性得到验证;
2、描述创建私有CA的过程,以及为客户端发来的证书请求进行办法证书。
答:
创建所需的文件:
[root@CA ~]# cd /etc/pki/CA/
[root@CA CA]# touch index.txt
[root@CA CA]# echo 01 > serial
[root@CA CA]# ls
certs crl index.txt newcerts private serial
[root@CA CA]# cat serial
01
CA自签证书:
[root@CA CA]# (umask 077; openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
[root@CA CA]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Guangdong
Locality Name (eg, city) [Default City]:Foshan
Organization Name (eg, company) [Default Company Ltd]:Mingcheng
Organizational Unit Name (eg, section) []:HR
Common Name (eg, your name or your server‘s hostname) []:CA.mc.com
Email Address []:caadmin@mc.com
-new: 生成新证书签署请求;
-x509: 专用于CA生成自签证书;
-key: 生成请求时用到的私钥文件;
-days n:证书的有效期限;
-out /PATH/TO/SOMECERTFILE: 证书的保存路径;
使用证书的主机生成证书请求:
[root@www ~]# (umask 077; openssl genrsa -out /etc/httpd/ssl/httpd.key 2048)
[root@www ~]# mkdir -pv /etc/httpd/ssl
[root@www ~]# cd /etc/httpd/ssl/
[root@www ssl]# openssl req -new -key httpd.key -days 365 -out httpd.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Guangdong
Locality Name (eg, city) [Default City]:Foshan
Organization Name (eg, company) [Default Company Ltd]:Mingcheng
Organizational Unit Name (eg, section) []:HR
Common Name (eg, your name or your server‘s hostname) []:www.mc.com
Email Address []:httpdadmin@mc.com
Please enter the following ‘extra‘ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@www ssl]# scp httpd.csr root@172.16.2.61:/tmp/
3)CA签署证书,并将证书发还给请求者:
[root@CA ~]# openssl ca -in /tmp/httpd.csr -out /etc/pki/CA/certs/httpd.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Mar 29 16:27:50 2017 GMT
Not After : Mar 29 16:27:50 2018 GMT
Subject:
countryName = CN
stateOrProvinceName = Guangdong
organizationName = Mingcheng
organizationalUnitName = HR
commonName = www.mc.com
emailAddress = httpdadmin@mc.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
D4:C0:D5:80:31:BF:B6:5E:46:49:14:77:13:BC:00:F1:14:26:CC:E2
X509v3 Authority Key Identifier:
keyid:CD:B1:39:86:AF:41:41:0C:BA:27:69:1D:69:2A:80:44:4C:4B:5C:81
Certificate is to be certified until Mar 29 16:27:50 2018 GMT (365 days)
Sign the certificate? [y/n]:y
[root@CA certs]# scp httpd.crt root@172.16.2.62:/etc/httpd/ssl/
3、搭建一套DNS服务器,负责解析magedu.com域名(自行设定主机名及IP)
(1)、能够对一些主机名进行正向解析和逆向解析;
(2)、对子域cdn.magedu.com进行子域授权,子域负责解析对应子域中的主机名;
(3)、为了保证DNS服务系统的高可用性,请设计一套方案,并写出详细的实施过程
答:
安装bind:
[root@dns ~]# yum -y install bind
修改主配置文件:
[root@dns etc]# vim named.conf
//
// named.conf
//
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
// server as a caching only nameserver (as a localhost DNS resolver only).
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
// See the BIND Administrator‘s Reference Manual (ARM) for details about the
// configuration located in /usr/share/doc/bind-{version}/Bv9ARM.html
options {
listen-on port 53 { 172.16.2.71; };
// listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { any; };
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-enable no;
dnssec-validation no;
/* Path to ISC DLV key */
// bindkeys-file "/etc/named.iscdlv.key";
// managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
在主配置文件/etc/named.rfc1912.zones中定义区域
[root@dns ~]# vim /etc/named.rfc1912.zones
增加如下内容:
zone "magedu.com" IN {
type master;
file "magedu.com.zone";
allow-update { none; };
};
zone "2.16.172.in-addr.arpa" IN {
type master;
file "2.16.172.zone";
allow-update { none; };
};
定义正向区域解析文件:
[root@dns ~]# vim /var/named/magedu.com.zone
$TTL 86400
$ORIGIN magedu.com.
@ IN SOA ns1.magedu.com. dnsadmin.magedu.com. (
2017033001
1H
2M
1W
1D )
IN NS ns1
IN NS ns2
IN MX 10 mail
ns1 IN A 172.16.2.71
ns2 IN A 172.16.2.72
www IN A 172.16.2.62
mail IN A 172.16.2.61
定义反向区域解析文件:
$TTL 86400
$ORIGIN 2.16.172.in-addr.arpa.
@ IN SOA ns1.magedu.com. dnsadmin.magedu.com. (
2017033001
1H
2M
1W
1D )
IN NS ns1.magedu.com.
IN NS ns2.magedu.com.
71 IN PTR ns1.magedu.com.
72 IN PTR ns2.magedu.com.
61 IN PTR mail.magedu.com.
62 IN PTR www.magedu.com.
修改区域解析文件的属组为named:
[root@dns ~]# chown :named /var/named/magedu.com.zone
[root@dns ~]# chown :named /var/named/2.16.172.zone
dig 查询结果:
[root@dns ~]# dig -t A www.magedu.com @172.16.2.71
; <<>> DiG 9.9.4-RedHat-9.9.4-38.el7_3.2 <<>> -t A www.magedu.com @172.16.2.71
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 48212
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.magedu.com. IN A
;; ANSWER SECTION:
www.magedu.com. 86400 IN A 172.16.2.62
;; AUTHORITY SECTION:
magedu.com. 86400 IN NS ns1.magedu.com.
magedu.com. 86400 IN NS ns2.magedu.com.
;; ADDITIONAL SECTION:
ns1.magedu.com. 86400 IN A 172.16.2.71
ns2.magedu.com. 86400 IN A 172.16.2.72
配置从DNS服务器,IP:172.16.2.72
[root@ns2 ~]# vim /etc/named.rfc1912.zones
zone "magedu.com" IN {
type slave;
masters { 172.16.2.71; };
file "slaves/magedu.com.zone";
};
zone "2.16.172.in-addr.arpa" IN {
type slave;
masters { 172.16.2.71; };
file "slaves/2.16.172.zone";
};
对子域cdn.magedu.com进行子域授权:
在父域magedu.com的解析文件中增加子域的内容:
cdn IN NS ns1.cdn
ns1.cdn IN A 172.16.2.73
新增子域DNS服务器,配置与父域基本相同:
[root@ns1 ~]# vim /etc/named.rfc1912.zones
zone "cdn.magedu.com" IN {
type master;
file "cdn.magedu.com.zone";
};
zone "magedu.com" IN {
type forward;
forward first;
forwarders { 172.16.2.71; };
};
[root@ns1 ~]# vim /var/named/cdn.magedu.com.zone
$TTL 86400
$ORIGIN cdn.magedu.com.
@ IN SOA ns1.cdn.magedu.com. admin.cdn.magedu.com. (
2017033001
1H
2M
1W
1D )
IN NS ns1
IN MX 10 mail
ns1 IN A 172.16.2.73
mail IN A 172.16.2.73
* IN A 172.16.2.73
在父域中解析子域:
[root@dns ~]# dig -t A mail.cdn.magedu.com @172.16.2.71
; <<>> DiG 9.9.4-RedHat-9.9.4-38.el7_3.2 <<>> -t A mail.cdn.magedu.com @172.16.2.71
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 54505
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;mail.cdn.magedu.com. IN A
;; ANSWER SECTION:
mail.cdn.magedu.com. 86400 IN A 172.16.2.73
;; AUTHORITY SECTION:
cdn.magedu.com. 86400 IN NS ns1.cdn.magedu.com.
;; ADDITIONAL SECTION:
ns1.cdn.magedu.com. 86400 IN A 172.16.2.73
;; Query time: 97 msec
;; SERVER: 172.16.2.71#53(172.16.2.71)
;; WHEN: Fri Mar 31 00:08:37 EDT 2017
;; MSG SIZE rcvd: 98
在子域中解析父域:
[root@ns1 ~]# dig -t A www.magedu.com @172.16.2.73
; <<>> DiG 9.9.4-RedHat-9.9.4-38.el7_3.2 <<>> -t A www.magedu.com @172.16.2.73
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 56581
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.magedu.com. IN A
;; ANSWER SECTION:
www.magedu.com. 86400 IN A 172.16.2.62
;; AUTHORITY SECTION:
magedu.com. 86400 IN NS ns2.magedu.com.
magedu.com. 86400 IN NS ns1.magedu.com.
;; ADDITIONAL SECTION:
ns1.magedu.com. 86400 IN A 172.16.2.71
ns2.magedu.com. 86400 IN A 172.16.2.72
;; Query time: 82 msec
;; SERVER: 172.16.2.73#53(172.16.2.73)
;; WHEN: Fri Mar 31 00:10:25 EDT 2017
;; MSG SIZE rcvd: 127
配置从DNS服务器:
4、请描述一次完整的http请求处理过程;
答:
(1)建立TCP连接
在http工作开始之前,web浏览器首先要通过TCP(传输控制协议)与web服务器建立连接;http是比tcp更高层次的应用层协议,根据规则,只有低层协议建立之后才能进行更高层协议的连接。因此,首先要建立TCP连接,默认TCP连接的端口号是80.
(2)Web浏览器想Web服务器发送请求命令
一旦建立了TCP连接,Web浏览器就会向Web服务器发送请求报文。如:GET /sample/hello.phpHTTP/1.1。
(3)Web浏览器发送请求头部信息
web浏览器给web服务器发送其请求命令之后,还要以头信息的形式向web服务器发送一些信息,然后再发送一空行(通知服务器头信息结束)。
(4)Web服务器响应
客户端想服务器发出请求后,服务器会给客户端会送应答,HTTP/1.1 200 OK,应答的第一部分是协议版本号和响应状态码。
(5)web服务器发送响应头信息
正如客户端会随同请求发送一些关于自身的信息一样,服务器也会随同响应向客户端发送关于它自身的数据及被请求的文档。
(6)Web服务器向浏览器发送数据
Web服务器向浏览器发送头部信息后,它会发送一个空白行来表示头部信息发送结束;接着,它就以ConTent-Type响应头部信息所描述的格式发送客户端所请求的实际数据。
(7)Web服务器关闭TCP连接
一般情况下,一旦Web服务器向浏览器发送了请求数据,它就要关闭TCP连接,但如果浏览器或服务器在其头部信息中加入了这行代码:Connection:keep-alive,TCP连接在发送后仍然保持打开状态;这样,浏览器可以继续通过相同的连接发送请求。保持连接节省了为每个请求建立新连接所需的时间,还节约了网络带宽。
5、httpd所支持的处理模型有哪些,他们的分别使用于哪些环境。
答:
httpd所支持的处理模型有prefork,worker,event;
prefork模型:多进程模型,每个进程响应一个请求;一个主进程:负责生成n个子进程,子进程也称为工作进程,每个子进程处理一个用户请求;即便没有用户请求,也会预先生成多个空闲进程,随时等待请求到达;子进程数最大不会超过1024个。
worker模型:多线程模型,每个线程响应一个请求;一个主进程:生成多个子进程,每个子进程负责生成多个线程,每个线程响应一个请求。m进程,n线程:最大的并发响应数是m*n。
httpd所支持的处理模型有prefork,worker,event;
6、建立httpd服务器(基于编译的方式进行),要求:
提供两个基于名称的虚拟主机:
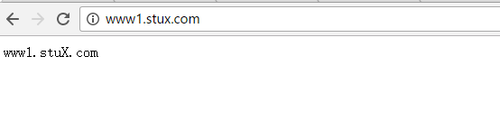
(a)www1.stuX.com,页面文件目录为/web/vhosts/www1;错误日志为/var/log/httpd/www1.err,访问日志为/var/log/httpd/www1.access;
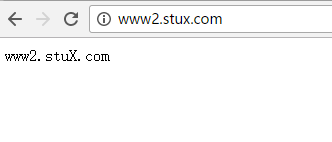
(b)www2.stuX.com,页面文件目录为/web/vhosts/www2;错误日志为/var/log/httpd/www2.err,访问日志为/var/log/httpd/www2.access;
(c)为两个虚拟主机建立各自的主页文件index.html,内容分别为其对应的主机名;
(d)通过www1.stuX.com/server-status输出httpd工作状态相关信息,且只允许提供帐号密码才能访问(status:status);
答:
安装必要的组件:
[root@localhost ~]# yum -y groupinstall "Desktop Platform Development" "Development tools" "Server Platform Development"
[root@localhost ~]# yum -y install pcre-devel
编译安装apr-1.5.2
[root@localhost ~]# tar vxf apr-1.5.2.tar.gz
[root@localhost ~]# cd apr-1.5.2
[root@localhost apr-1.5.2]# ./configure --prefix=/usr/local/apr
[root@localhost apr-1.5.2]# make && make install
编译安装apr-util-1.5.4
[root@localhost ~]# tar xf apr-util-1.5.4.tar.gz
[root@localhost ~]# cd apr-util-1.5.4
[root@localhost apr-util-1.5.4]# ./configure --prefix=/usr/local/apr-util --with-apr=/usr/local/apr/
[root@localhost apr-util-1.5.4]# make && make install
创建apache账号:
[root@localhost ~]# groupadd -r apache
[root@localhost ~]# useradd -r -g apache -s /sbin/nologin apache
编译安装httpd-2.4.25:
[root@localhost ~]# tar xf httpd-2.4.25.tar.gz
[root@localhost httpd-2.4.25]# ./configure --prefix=/usr/local/apache --sysconf=/etc/httpd24 --enable-so --enable-ssl --enable-cgi --enable-rewrite --with-zlib --with-pcre --with-apr=/usr/local/apr --with-apr-util=/usr/local/apr-util/ --enable-modules=most --enable-mpms-shared=all --with-mpm=prefork
[root@localhost ~]# make && make install
为httpd提供服务脚本:
[root@localhost ~]# cd /etc/init.d/
[root@localhost init.d]# vim httpd24
#!/bin/bash
#
# httpd Startup script for the Apache HTTP Server
#
# chkconfig: - 85 15
# description: The Apache HTTP Server is an efficient and extensible \
# server implementing the current HTTP standards.
# processname: httpd
# config: /etc/httpd/conf/httpd.conf
# config: /etc/sysconfig/httpd
# pidfile: /var/run/httpd/httpd.pid
#
### BEGIN INIT INFO
# Provides: httpd
# Required-Start: $local_fs $remote_fs $network $named
# Required-Stop: $local_fs $remote_fs $network
# Should-Start: distcache
# Short-Description: start and stop Apache HTTP Server
# Description: The Apache HTTP Server is an extensible server
# implementing the current HTTP standards.
### END INIT INFO
# Source function library.
. /etc/rc.d/init.d/functions
if [ -f /etc/sysconfig/httpd ]; then
. /etc/sysconfig/httpd
fi
# Start httpd in the C locale by default.
HTTPD_LANG=${HTTPD_LANG-"C"}
# This will prevent initlog from swallowing up a pass-phrase prompt if
# mod_ssl needs a pass-phrase from the user.
INITLOG_ARGS=""
# Set HTTPD=/usr/sbin/httpd.worker in /etc/sysconfig/httpd to use a server
# with the thread-based "worker" MPM; BE WARNED that some modules may not
# work correctly with a thread-based MPM; notably PHP will refuse to start.
# Path to the apachectl script, server binary, and short-form for messages.
apachectl=/usr/local/apache/bin/apachectl
httpd=/usr/local/apache/bin/httpd
prog=httpd
pidfile=${PIDFILE-/var/run/httpd24.pid}
lockfile=${LOCKFILE-/var/lock/subsys/httpd24}
RETVAL=0
STOP_TIMEOUT=${STOP_TIMEOUT-10}
# The semantics of these two functions differ from the way apachectl does
# things -- attempting to start while running is a failure, and shutdown
# when not running is also a failure. So we just do it the way init scripts
# are expected to behave here.
start() {
echo -n $"Starting $prog: "
LANG=$HTTPD_LANG daemon --pidfile=${pidfile} $httpd $OPTIONS
RETVAL=$?
echo
[ $RETVAL = 0 ] && touch ${lockfile}
return $RETVAL
}
# When stopping httpd, a delay (of default 10 second) is required
# before SIGKILLing the httpd parent; this gives enough time for the
# httpd parent to SIGKILL any errant children.
stop() {
echo -n $"Stopping $prog: "
killproc -p ${pidfile} -d ${STOP_TIMEOUT} $httpd
RETVAL=$?
echo
[ $RETVAL = 0 ] && rm -f ${lockfile} ${pidfile}
}
reload() {
echo -n $"Reloading $prog: "
if ! LANG=$HTTPD_LANG $httpd $OPTIONS -t >&/dev/null; then
RETVAL=6
echo $"not reloading due to configuration syntax error"
failure $"not reloading $httpd due to configuration syntax error"
else
# Force LSB behaviour from killproc
LSB=1 killproc -p ${pidfile} $httpd -HUP
RETVAL=$?
if [ $RETVAL -eq 7 ]; then
failure $"httpd shutdown"
fi
fi
echo
}
case "$1" in
start)
start
;;
stop)
stop
;;
status)
status -p ${pidfile} $httpd
RETVAL=$?
;;
restart)
stop
start
;;
condrestart|try-restart)
if status -p ${pidfile} $httpd >&/dev/null; then
stop
start
fi
;;
force-reload|reload)
reload
;;
graceful|help|configtest|fullstatus)
$apachectl $@
RETVAL=$?
;;
*)
echo $"Usage: $prog {start|stop|restart|condrestart|try-restart|force-reload|reload|status|fullstatus|graceful|help|configtest}"
RETVAL=2
esac
exit $RETVAL
[root@localhost init.d]# chmod +x httpd24
关闭selinux和防火墙:
[root@localhost subsys]# setenforce 0
[root@localhost subsys]# service iptables stop
启用虚拟主机,禁用中心主机
[root@localhost ~]# vim /etc/httpd24/httpd.conf
# Virtual hosts
Include/etc/httpd24/extra/httpd-vhosts.conf
#DocumentRoot"/usr/local/apache/htdocs"
添加两个虚拟主机:
[root@localhost ~]# vim /etc/httpd24/extra/httpd-vhosts.conf
<VirtualHost *:80>
DocumentRoot /web/vhosts/www1
ServerName www1.stuX.com
ErrorLog "/var/log/httpd/www1.err"
CustomLog "/var/log/httpd/www1.access" common
<Directory "/vhosts/www1.stuX.com">
<RequireAll>
Require all granted
</RequireAll>
</Directory>
<Location /server-status>
SetHandler server-status
Authtype Basic
Authname "status"
AuthUserFile /etc/httpd24/.htpasswd
Require valid-user
</Location>
</VirtualHost>
<VirtualHost *:80>
DocumentRoot /web/vhosts/www2
ServerName www2.stuX.com
ErrorLog "/var/log/httpd/www2.err"
CustomLog "/var/log/httpd/www2.access" common
<Directory "/vhosts/www2.stuX.com">
<RequireAll>
Require all granted
</RequireAll>
</Directory>
</VirtualHost>
创建网站主页文件:
[root@localhost ~]# cd /web/vhosts/www1/
[root@localhost www1]# vim index.html
[root@localhost vhosts]# cd www2/
[root@localhost www2]# vim index.html
创建用户认证的数据库文件:
[root@localhost bin]# ./htpasswd -c -m /etc/httpd24/.htpasswd status
[root@localhost ~]# service httpd24 start
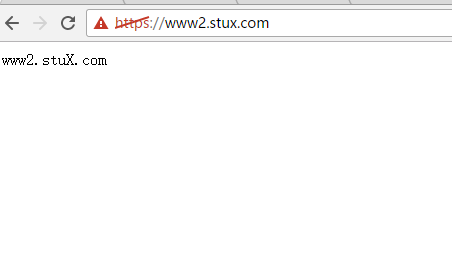
7、为第6题中的第2个虚拟主机提供https服务,使得用户可以通过https安全的访问此web站点;
(1)要求使用证书认证,证书中要求使用的国家(CN)、州(HA)、城市(ZZ)和组织(MageEdu);
(2)设置部门为Ops,主机名为www2.stuX.com,邮件为admin@stuX.com;
答:
建立私有CA并生成一个自签署证书:
[root@localhost CA]# (umask 077; openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
Generating RSA private key, 2048 bit long modulus
..........+++
......................................................................+++
e is 65537 (0x10001)
[root@localhost CA]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HA
Locality Name (eg, city) [Default City]:ZZ
Organization Name (eg, company) [Default Company Ltd]:MageEdu
Organizational Unit Name (eg, section) []:Ops
Common Name (eg, your name or your server‘s hostname) []:CA.stuX.com
Email Address []:admin@stuX.com
在使用证书的主机上生成CA请求:
[root@localhost ssl]# (umask 077; openssl genrsa -out /usr/local/apache/ssl/httpd.key 2048)
Generating RSA private key, 2048 bit long modulus
...+++
..................+++
e is 65537 (0x10001)
[root@localhost ssl]# openssl req -new -key /usr/local/apache/ssl/httpd.key -days 365 -out /usr/local/apache/ssl/www2.stuX.com.crs
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HA
Locality Name (eg, city) [Default City]:ZZ
Organization Name (eg, company) [Default Company Ltd]:MageEdu
Organizational Unit Name (eg, section) []:Ops
Common Name (eg, your name or your server‘s hostname) []:www2.stuX.com
Email Address []:admin@stuX.com
Please enter the following ‘extra‘ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
发送证书请求至CA:
[root@localhost ssl]# scp www2.stuX.com.crs root@192.168.1.63:/tmp
CA签署证书:
[root@localhost CA]# openssl ca -in /tmp/www2.stuX.com.crs -out certs/www2.stuX.com.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Apr 2 11:21:35 2017 GMT
Not After : Apr 2 11:21:35 2018 GMT
Subject:
countryName = CN
stateOrProvinceName = HA
organizationName = MageEdu
organizationalUnitName = Ops
commonName = www2.stuX.com
emailAddress = admin@stuX.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
8E:DB:84:7F:75:01:55:F6:75:2C:4F:3C:4B:FE:73:2A:62:72:C0:77
X509v3 Authority Key Identifier:
keyid:6E:1F:73:FE:78:52:76:FB:05:FA:3B:5F:FD:EC:FB:E7:ED:F3:B8:46
Certificate is to be certified until Apr 2 11:21:35 2018 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
把证书发给申请主机:
[root@localhost certs]# scp www2.stuX.com.crt root@192.168.1.62:/usr/local/apache/ssl/
修改httpd.conf配置文件,启用SSL模块:
Include /etc/httpd24/extra/httpd-ssl.conf
LoadModule ssl_module modules/mod_ssl.so
LoadModule socache_shmcb_module modules/mod_socache_shmcb.so
添加httpd中ssl配置:
[root@localhost ~]# vim /etc/httpd24/extra/httpd-ssl.conf
<VirtualHost *:443>
# General setup for the virtual host
DocumentRoot "/web/vhosts/www2"
ServerName www2.stuX.com
ServerAdmin admin@stuX.com
<Directory "/web/vhosts/www2">
<RequireAll>
Require all granted
</RequireAll>
</Directory>
SSLCertificateFile "/usr/local/apache/ssl/www2.stuX.com.crt"
SSLCertificateKeyFile "/usr/local/apache/ssl/httpd.key"
8、建立samba共享,共享目录为/data,要求:(描述完整的过程)
1)共享名为shared,工作组为magedu;
2)添加组develop,添加用户gentoo,centos和ubuntu,其中gentoo和centos以develop为附加组,ubuntu不属于develop组;密码均为用户名;
3)添加samba用户gentoo,centos和ubuntu,密码均为“mageedu”;
4)此samba共享shared仅允许develop组具有写权限,其他用户只能以只读方式访问;
5)此samba共享服务仅允许来自于172.16.0.0/16网络的主机访问;
答:
[root@localhost /]# groupadd develop
[root@localhost /]# useradd -G develop gentoo
[root@localhost /]# useradd -G develop centos
[root@localhost /]# useradd ubuntu
[root@localhost /]# echo gentoo | passwd --stdin gentoo
[root@localhost /]# echo centos | passwd --stdin centos
[root@localhost /]# echo ubuntu | passwd --stdin ubuntu
[root@localhost /]# smbpasswd -a gentoo
[root@localhost /]# smbpasswd -a centos
[root@localhost /]# smbpasswd -a ubuntu
[root@localhost /]# vim /etc/samba/smb.conf
hosts allow = 172.16.
[share]
comment = share
path = /share
public = no
writable = yes
write list = +develop
[root@localhost ~]# smbclient //172.16.1.72/share -U centos
Enter centos‘s password:
Domain=[MYGROUP] OS=[Windows 6.1] Server=[Samba 4.2.10]
smb: \> ls
. D 0 Sat Apr 02 17:20:02 2017
.. DR 0 Sat Apr 02 17:20:02 2017
77931220 blocks of size 1024. 71904540 blocks available
smb: \> lcd /etc
smb: \> put passwd
putting file passwd as \passwd (946.6 kb/s) (average 946.6 kb/s)
[root@localhost ~]# smbclient //172.16.1.72/share -U ubuntu
Enter ubuntu‘s password:
Domain=[MYGROUP] OS=[Windows 6.1] Server=[Samba 4.2.10]
smb: \> lcd
smb: \> lcd /etc
smb: \> put fstab
NT_STATUS_ACCESS_DENIED opening remote file \fstab
9、搭建一套文件vsftp文件共享服务,共享目录为/ftproot,要求:(描述完整的过程)
1)基于虚拟用户的访问形式;
2)匿名用户只允许下载,不允许上传;
3)禁锢所有的用户于其家目录当中;
4)限制最大并发连接数为200:;
5)匿名用户的最大传输速率512KB/s
6)虚拟用户的账号存储在mysql数据库当中。
7)数据库通过NFS进行共享。
马哥第六次作业
