首页 > 代码库 > CA认证的具体实验步骤
CA认证的具体实验步骤
博文目录
CA认证的配置文件是/etc/pki/tls/opensl.cnf
服务器的操作
1.进入/etc/pki/CA下
创建 index.txt,serial,crlnumber这三个文件 并为为创建记录证书文件和吊销证书文件给予编号 [root@centos6 ~]# cd /etc/pki/CA [root@centos6 CA]# touch index.txt [root@centos6 CA]# touch serial [root@centos6 CA]# touch crlnumber [root@centos6 CA]# echo 01 > serial [root@centos6 CA]# echo 01 > crlnumber
2.建立私钥文件
[root@centos6 CA]# (umask 077 ; openssl genrsa -out /etc/pki/CA/private/cakey.pem 4096 ) Generating RSA private key, 4096 bit long modulus ..................................................++ .....................................................................................................................................................................................++ e is 65537 (0x10001) #()代表建立一个子shell,umask 077 改变子shell的权限 #openssl genrsa -out 输入一个密钥文件 长度为4096 [root@centos6 CA]# tree #查看CA目录下的文件 . ├── cacert.pem ├── certs ├── crl ├── crlnumber ├── index.txt ├── newcerts ├── private │ └── cakey.pem └── serial 4 directories, 5 files
3.给自己颁发CA认证
[root@centos6 CA]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 36500 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.‘, the field will be left blank. ----- Country Name (2 letter code) [XX]:CN # 国家 State or Province Name (full name) []:beijing # 省/州 Locality Name (eg, city) [Default City]:beijing # 城市 Organization Name (eg, company) [Default Company Ltd]:bta # 公司 Organizational Unit Name (eg, section) []:yunwei # 部门 Common Name (eg, your name or your server‘s hostname) []:bta.com # 所需要认证的名称 Email Address []:123@123.com # Email
客户端
客户端需要在/etc/pki/tls/下操作
1.进入 /etc/pki/tls建立私钥文件
[root@go ~]$cd /etc/pki/tls/ [root@go tls]$(umask 077; openssl genrsa -out /etc/pki/tls/private/TianRandai.key 2048) Generating RSA private key, 2048 bit long modulus ....+++ ..+++ e is 65537 (0x10001 [root@go tls]$tree private/ #查看TianRandai.key是否创建成功 private/ └── TianRandai.key 0 directories, 1 file
2.导出证书
root@go tls]$openssl req -new -key private/TianRandai.key -out TianRandai.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.‘, the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:beijing Locality Name (eg, city) [Default City]:beijing Organization Name (eg, company) [Default Company Ltd]:bta Organizational Unit Name (eg, section) []:yunwei Common Name (eg, your name or your server‘s hostname) []:www.bta.com Email Address []:12@123.com Please enter the following ‘extra‘ attributes to be sent with your certificate request A challenge password []: An optional company name []: #这里的内容需要和服务端match的地方填写相同的信息
3.将证书复制到服务端
[root@go tls]$scp TianRandai.csr 172.18.17.21:/etc/pki/CA root@172.18.17.21‘s password: TianRandai.csr 100% 1041 1.0KB/s 00:00
服务端
1.查看一下客户端文件
[root@centos6 CA]# tree . ├── cacert.pem ├── certs ├── crl ├── crlnumber ├── index.txt ├── newcerts ├── private │ └── cakey.pem ├── serial └── TianRandai.csr
#客户端文件已经拷贝过来了
4 directories, 6 files
2.认证客户端文件生成CA证书
[root@centos6 CA]# openssl ca -in TianRandai.csr -out TianRandai.crt -days 365 #-days 给予证书的期限,默认以天为单位 Using configuration from /etc/pki/tls/openssl.cnf Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Feb 21 01:57:04 2017 GMT Not After : Feb 21 01:57:04 2018 GMT Subject: countryName = CN stateOrProvinceName = beijing organizationName = bta organizationalUnitName = yunwei commonName = www.bta.com emailAddress = 12@123.com X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 2C:2E:03:82:0A:2C:95:11:7E:0F:71:DC:41:B8:B6:F8:F3:32:3B:1F X509v3 Authority Key Identifier: keyid:98:9B:95:79:0B:0A:25:93:17:06:D1:02:92:1A:EF:A0:6F:6B:95:D8 Certificate is to be certified until Feb 21 01:57:04 2018 GMT (365 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated
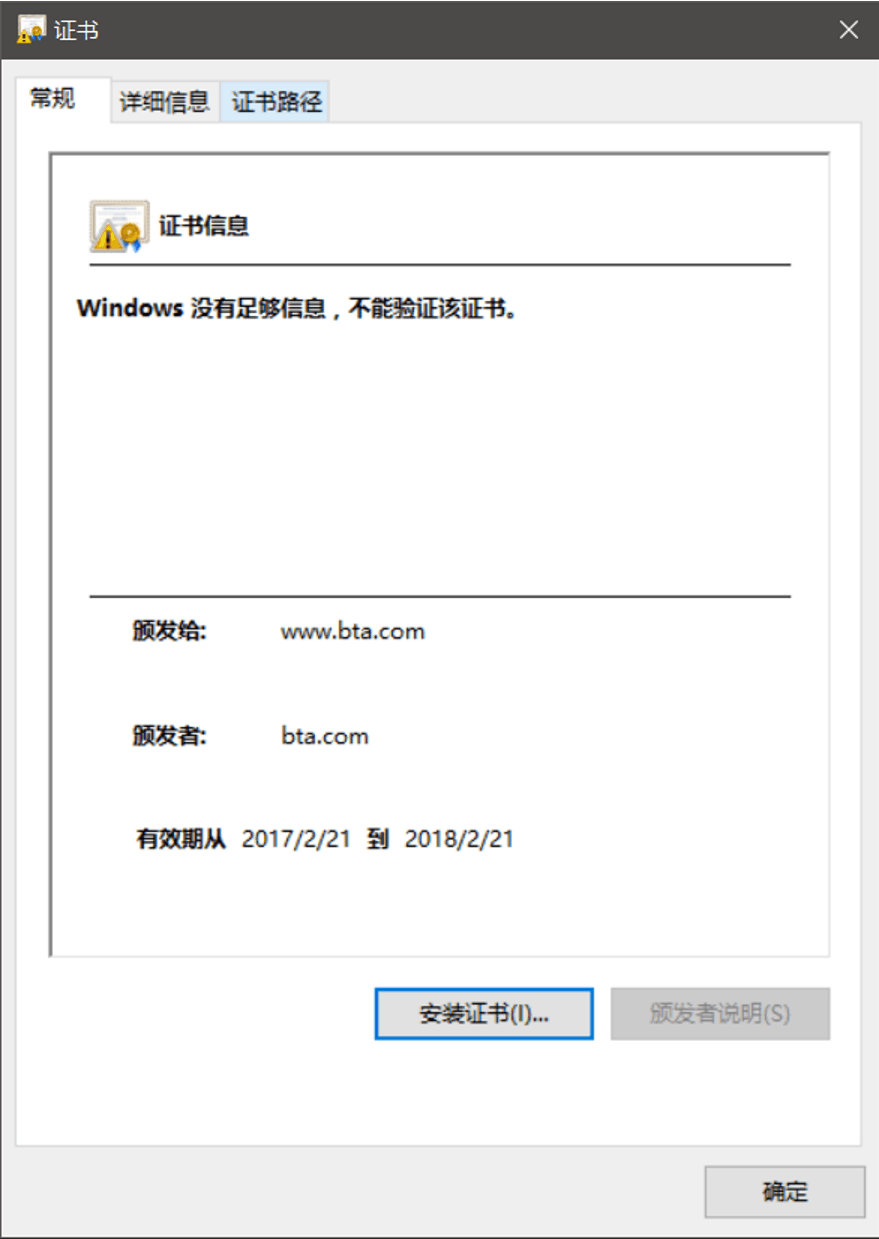
3.拷贝到windows上来开一看,木有问题
本文出自 “12612752” 博客,请务必保留此出处http://12622752.blog.51cto.com/12612752/1915033
CA认证的具体实验步骤
声明:以上内容来自用户投稿及互联网公开渠道收集整理发布,本网站不拥有所有权,未作人工编辑处理,也不承担相关法律责任,若内容有误或涉及侵权可进行投诉: 投诉/举报 工作人员会在5个工作日内联系你,一经查实,本站将立刻删除涉嫌侵权内容。
