首页 > 代码库 > ASA防火墙配置案例(一)
ASA防火墙配置案例(一)
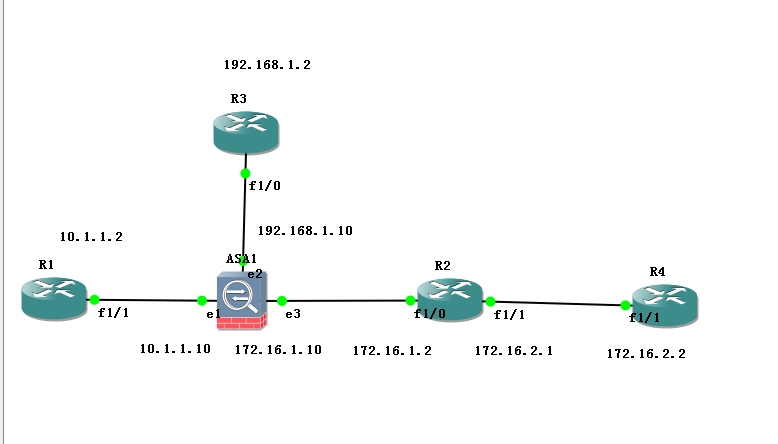
实验目标:
1.配置静态路由,实现全网互通。
2.R1能telnet到R3,R4,R3被拒绝ACL规则telnet到R4,R4无法telnet到R1和R3.
ASA
en
conf t
int e0/1
nameif inside
security-level 100
ip add 10.1.1.10 255.255.255.0
no sh
int e0/2
nameif dmz
security-level 50
ip address 192.168.1.10 255.255.255.0
no sh
int e0/3
nameif outside
security-level 0
ip add 172.16.1.10 255.255.255.0
no sh
exit
route outside 172.16.2.0 255.255.255.0 172.16.1.2
access-list r3-r4 deny ip host 192.168.1.2 host 172.16.2.2
access-group r3-r4 in interface dmz
R1
en
conf t
hostname router1
int f1/1
no sw
ip address 10.1.1.2 255.255.255.0
no sh
exit
ip routing
ip route 172.16.1.0 255.255.255.0 10.1.1.10
ip route 172.16.2.0 255.255.255.0 10.1.1.10
ip route 192.168.1.0 255.255.255.0 10.1.1.10
line vty 0 4
password 123456
login
exit
R2
en
conf t
hostname router2
int f1/0
no sw
ip address 172.16.1.2 255.255.255.0
no sh
int f1/1
no sw
ip address 172.16.2.1 255.255.255.0
no sh
exit
ip route 192.168.1.0 255.255.255.0 172.16.1.10
ip route 10.1.1.0 255.255.255.0 172.16.1.10
end
R3
en
conf t
hostname router3
int f1/0
no sw
ip address 192.168.1.2 255.255.255.0
no sh
exit
ip route 172.16.1.0 255.255.255.0 192.168.1.10
ip route 172.16.2.0 255.255.255.0 192.168.1.10
ip route 10.1.1.0 255.255.255.0 192.168.1.10
line vty 0 4
password 123456
login
exit
R4
en
conf t
hostname router4
int f1/1
no sw
ip address 172.16.2.2 255.255.255.0
no sh
exit
ip route 192.168.1.0 255.255.255.0 172.16.2.1
ip route 10.1.1.0 255.255.255.0 172.16.2.1
ip route 172.16.1.0 255.255.255.0 172.16.2.1
line vty 0 4
password 123456
login
exit
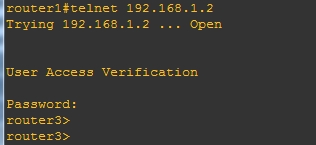
R1telnet到R3
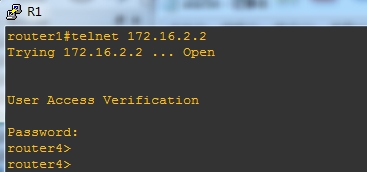
2.R1 telnet 到 R4
3.R4无法telnet到R1,R3。
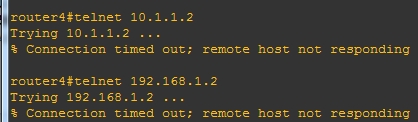
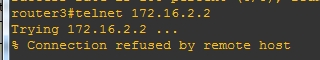
4.R3因为ACL被拒绝telnet到R4
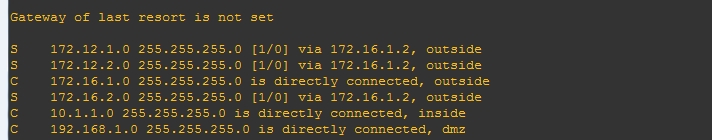
5.查看ASA防火墙的路由表。
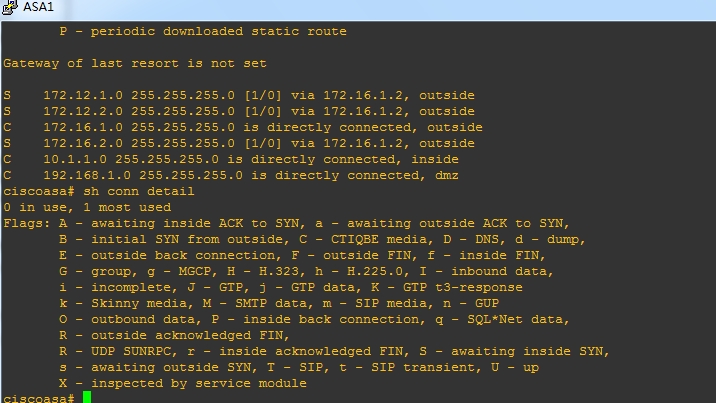
6.show conn detail。
本文出自 “龙爱雪琪” 博客,谢绝转载!
ASA防火墙配置案例(一)
