首页 > 代码库 > VLAN+trunk+端口安全组合实验一
VLAN+trunk+端口安全组合实验一
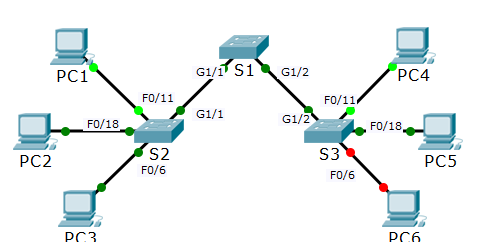
Scenario
In this activity, two switches are completely configured. On a third switch, you are responsible for assigning IP addressing to the Switch Virtual Interface, configuring VLANs, assigning VLANs to interfaces, configuring trunking, and performing basic switch security.
Requirements
S1 and S2 are fully configured. You cannot access these switches. You are responsible for configuring S3 with the following requirements:
· IP addressing and default gateway configuration, according to the Addressing Table.
· Create, name, and assign VLANs according to the VLANs and Port Assignment Table.
· Assign the native VLAN 99 to the trunk port and disable DTP.
· Restrict the trunk to only allow VLANs 10, 20, 30, 88, and 99.
· Use VLAN 99 as the native VLAN on the trunk ports.
· Configure basic switch security on S1.
- Encrypted secret password of itsasecret
- Console password of letmein
- VTY password of c1$c0 (where 0 is the number zero)
- Encrypted plain text passwords
- MOTD banner with the message Authorized Access Only!!
- Disable unused ports.
· Configure port security on F0/6.
- Only two unique devices are allowed to access the port.
- Learned MACs are added to the running configuration.
- Secure the interface so that a notification is sent when there is a violation, but the port is not disabled.
· Verify the PCs in the same VLAN can now ping each other.
相应命令:
S3>enable
S3#conf t
S3(config)#vlan 88
S3(config-vlan)#name Management
S3(config-vlan)#exit
S3(config)#int
S3(config)#interface vl
S3(config)#interface vlan 88
S3(config-if)#ip address  172.31.88.4
172.31.88.4  255.255.255.0
255.255.255.0
S3(config-if)#no shutdown
S3(config)#ip default-gateway  172.31.88.1
172.31.88.1
S3(config)#vlan 10
S3(config-vlan)#name Sales
S3(config-vlan)#exit
S3(config)#vlan 20
S3(config-vlan)#na Production
S3(config-vlan)#exit
S3(config)#vlan 30
S3(config-vlan)#name Marketing
S3(config-vlan)#exit
S3(config)#vlan 99
S3(config-vlan)#name Native
S3(config-vlan)#exit
S3(config)#interface gigabitEthernet 0/2
S3(config-if)#switchport native vlan 99
S3(config-if)#exit
S3(config)#interface gigabitEthernet 0/2
S3(config-if)#switchport nonegotiate
S3(config-if)#exit
S3(config)#interface r f0/7-12
S3(config-if-range)#sw
S3(config-if-range)#switchport mo ac
S3(config-if-range)#sw ac vl 10
S3(config-if-range)#exit
S3(config)#int r f0/13-20
S3(config-if-range)#sw mo ac
S3(config-if-range)#sw ac vl 20
S3(config-if-range)#exit
S3(config)#int r f0/1-6
S3(config-if-range)#sw mo ac
S3(config-if-range)#sw ac vl 30
S3(config-if-range)#exit
S3(config)#int g0/2
S3(config-if)#sw
S3(config-if)#switchport na
S3(config-if)#switchport native vl 99
S3(config-if)#switchport tr allowed vl 10,20,30,88,99
S3(config-if)#switchport mo tr
S3(config-if)#exit
S3(config)#enable secret itsasecret
S3(config)#service password-encryption
S3(config)#line console 0
S3(config-line)#password letmein
S3(config-line)#exit
S3(config)#line vty 0
S3(config-line)#password c1$c0
S3(config-line)#exit
S3(config)#service password-encryption
S3(config)#banner motd ‘ Authorized Access Only!!‘
S3(config)#exit
S3#conf t
S3(config)#interface range fastEthernet 0/1-5
S3(config-if-range)#sh
S3(config-if-range)#shutdown
S3(config-if-range)#exit
S3(config)#interface range fastEthernet 0/7-10
S3(config-if-range)#sh
S3(config-if-range)#shutdown
S3(config-if-range)#exit
S3(config)#interface range fastEthernet 0/12-17
S3(config-if-range)#shutdown
S3(config-if-range)#exit
S3(config)#interface range fastEthernet 0/19-24
S3(config-if-range)#shutdown
S3(config-if-range)#exit
S3(config)#interface gigabitEthernet 0/1
S3(config-if)#shutdown
S3(config)#interface fastEthernet 0/6
S3(config-if)#shutdown
S3(config-if)#switchport port-security
S3(config-if)#switchport port-security maximum 2
S3(config-if)#switchport port-security mac-address sticky
S3(config-if)#switchport port-security violation restrict
本文出自 “一颗正在成长的小树” 博客,请务必保留此出处http://growing2015.blog.51cto.com/12006344/1919781
VLAN+trunk+端口安全组合实验一
