首页 > 代码库 > OpenSSL配置Apache的https功能
OpenSSL配置Apache的https功能
https:会话建立过程
1.客户端和服务器端先三次握手
2.客户端发起请求,请求服务器端的443端口。
3.双方协商建立ssl会话
4.协商完成后,服务器发送自己的证书给客户端。
5.客户端拿到证书后,查看证书是不是受信任证书颁发机构颁发的,和验证证书是不是完整的。
6.客户端传递加密后的对称密码给服务器端。
连接建立完成
CA给客户端颁发证书过程
1.创建CA
自己生成一对密钥
生成自签名证书
2.客户端
生成一对密钥
生成证书颁发请求,.csr
将请求发给CA
3.CA端
签署此证书
传送给客户端
注意:SSL仅能基于Ip地址进行,如果有多个虚拟主机的话,那么只能给其中一个加密
实验部分
查看httpd模块,确保有ssl,如果没有就手动安装
[root@localhost ~]# httpd -M
ssl_module
查看ssl生成的文件
[root@localhost ~]# rpm -ql mod_ssl
/etc/httpd/conf.d/ssl.conf #ssl主配置文件
/usr/lib/httpd/modules/mod_ssl.so #安装了一个ssl模块
/var/cache/mod_ssl #ssl缓存目录
建立私有证书颁发机构
生成Ca的私钥
[root@localhost ~]# cd /etc/pki/CA/
[root@localhost CA]# (umask 077; openssl genrsa -out private/cakey.pem 2048)
Generating RSA private key, 2048 bit long modulus
.....................................+++
.........................+++
e is 65537 (0x10001)
[root@localhost CA]#
使用私钥生产自签名证书
[root@localhost CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
-----
Country Name (2 letter code) [GB]:CN #设置国家名称
State or Province Name (full name) [Berkshire]:HB #设置省份名称
Locality Name (eg, city) [Newbury]:SJG #设置市名称
Organization Name (eg, company) [My Company Ltd]:BENET #设置组织名称
Organizational Unit Name (eg, section) []:LB #设置部门名称
Common Name (eg, your name or your server‘s hostname) []:www.benet.com #设置主机名需要与颁发的主机名一直,不然会报证书不信任
Email Address []:ca@benet.com #设置电子邮件地址
编辑配置文件***的存放位置
[root@localhost ~]# vim /etc/pki/tls/openssl.cnf
dir = /etc/pki/CA
准备三个目录,证书颁发目录(certs),证书吊销(crl),刚生成的证书(newcerts)和颁发证书的序列号文件index.txt并且写入第一个证书序列号为01
[root@localhost CA]# mkdir certs crl newcerts
[root@localhost CA]# touch index.txt
[root@localhost CA]# echo 01 > serial
这个时候CA就可以用了
web服务器配置
准备一个目录存储证书
[root@localhost CA]# cd /etc/httpd/
[root@localhost httpd]# mkdir ssl
[root@localhost httpd]# cd ssl/
生成web的私钥证书
[root@localhost ssl]# (umask 077;openssl genrsa 1024 > httpd.key)
Generating RSA private key, 1024 bit long modulus
............++++++
..........................++++++
e is 65537 (0x10001)
生成证书签署请求
[root@localhost ssl]# openssl req -new -key httpd.key -out httpd.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
-----
Country Name (2 letter code) [GB]:CN
State or Province Name (full name) [Berkshire]:HB
Locality Name (eg, city) [Newbury]:SJZ
Organization Name (eg, company) [My Company Ltd]:BENET
Organizational Unit Name (eg, section) []:LB
Common Name (eg, your name or your server‘s hostname) []:www.benet.com #和网站的域名必须保持完全一致
Email Address []:aa@benet.com
Please enter the following ‘extra‘ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
CA服务器签署web服务器的证书
[root@localhost ~]# openssl ca -in /etc/httpd/ssl/httpd.csr -out /etc/httpd/ssl/httpd.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Nov 26 10:42:56 2014 GMT
Not After : Nov 26 10:42:56 2015 GMT
Subject:
countryName = CN
stateOrProvinceName = HB
organizationName = BENET
organizationalUnitName = LB
commonName = www.benet.com
emailAddress = aa@benet.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
35:F3:EE:62:1F:64:D5:06:DB:5C:60:77:0B:19:33:C2:6A:8B:2D:B4
X509v3 Authority Key Identifier:
keyid:57:72:4C:91:1C:9B:F2:B0:E8:4A:E1:34:AB:03:E6:E6:31:2A:1D:C3
Certificate is to be certified until Nov 26 10:42:56 2015 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
查看颁发情况
[root@localhost CA]# cat index.txt
V 151126104256Z 01 unknown /C=CN/ST=HB/O=BENET/OU=LB/CN=www.benet.com/emailAddress=aa@benet.com
查看下一个请求给的序列号
[root@localhost CA]# cat serial
02
证书申请完毕
客户端配置ssl
配置之前先备份配置文件
[root@localhost ssl]# cd /etc/httpd/conf.d/
[root@localhost conf.d]# cp ssl.conf ssl.conf.bak
编辑ssl配置文件,除了列出的需要设置,其他统统不管
<VirtualHost 192.168.0.108:443>
ServerName www.benet.com #设置网站域名
DocumentRoot "/www/benet.com" #设置网站存放位置
ErrorLog logs/ssl_error_log #设置网站错误日志
TransferLog logs/ssl_access_log #设置网站访问日志
LogLevel warn #设置警告级别
SSLEngine on #是否开启ssl功能
SSLProtocol all -SSLv2 #支持的协议为,不支持sslv2,然后支持所有
SSLCertificateFile /etc/httpd/ssl/httpd.crt #设置证书文件位置
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key #设置私钥文件位置
</VirtualHost>
编辑完成之后重新启动httpd服务,然后查看443端口已经启动了
[root@localhost conf.d]# service httpd restart
[root@localhost conf.d]# netstat -tnlp
tcp 0 0 :::443 :::* LISTEN 6436/httpd
这时客户端访问www.benet.com的443端口还是会报错,这时因为客户端不信任CA颁发机构
需要将/etc/pki/CA/cacert.pem文件复制到客户端
并且客户端改名为cacert.crt,然后安装证书,并且放到根颁发机构
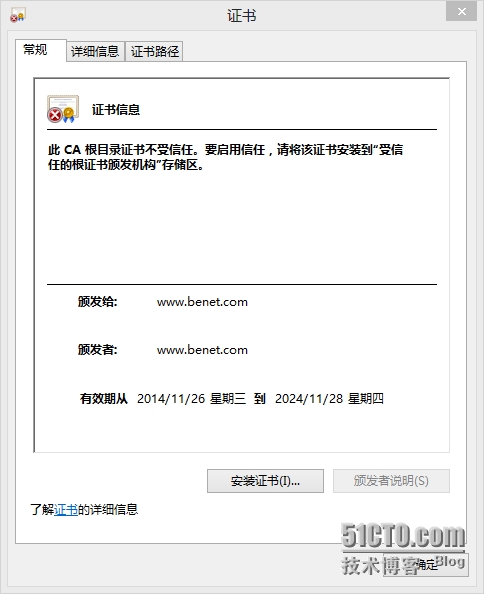
这时客户端在访问就不会报错了,而且访问全部是加密的访问了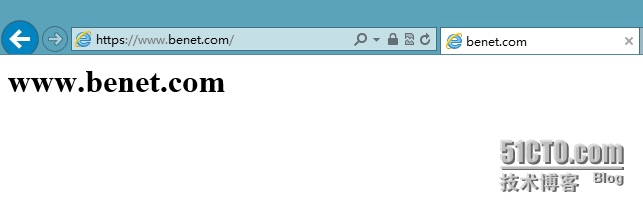
本文出自 “梅花香自苦寒来” 博客,请务必保留此出处http://wangjunkang.blog.51cto.com/8809812/1583306
OpenSSL配置Apache的https功能
