首页 > 代码库 > DNS配置安装和DNS主从配置
DNS配置安装和DNS主从配置
dns介绍 (用来解析域名的)
dns==domain name server(域名服务器)
DNS 全称domain name system域名系统的缩写,它是一种将IP地址转换成对应的主机名或者将主机名转换成对应的IP的一种服务机制。其中通过域名解析出IP叫做正向解析,通过IP解析出域名叫做反向解析。DNS使用TCP和UDP协议,端口号都是53,但它主要使用UDP,服务器之间备份使用TCP。全世界只有13台“根”服务器,一个主根服务器放在美国,其他12台为辅根服务器,DNS服务器根据角色可分为:主DNS,从DNS,缓存DNS服务器,DNS转发服务器。
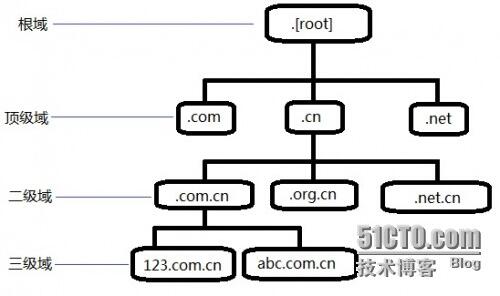
首先来看看域名的结构组成,我们平时访问网站的时候,都会用一个域名去请求,比如www.baidu.com,其实.com后面还有一个点,这个点叫做根域。下图是一个域名的树状结构,根域下面会有.com,.cn,.net等顶级域,顶级域下面又有二级域名,比如baidu.com或者.com.cn等,而www.baidu.com则为子域,我们经常用子域来做网站的域名。
早期的域名到IP的映射是保存在hosts文件中的:
[root@cp1 ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
DNS解析过程:先在本地/etc/hosts文件中查找解析,如果找到直接使用;如果找不到,则进行下图所示的解析过程:

查看DNS配置文件的内容:
[root@cp1 ~]# cat /etc/resolv.conf
; generated by /sbin/dhclient-script
search localdomain
nameserver 192.168.147.2
我们使用bind来搭建DNS服务,
首先安装bind:
[root@cp1 ~]# yum install -y bind
配置文件说明:
主配置文件:/etc/named.conf
(监听的端口53,IP127.0.0.1)
域服务器配置文件:/var/named/named.ca
本地主机配置文件:/var/named/named.localhost
反解析配置文件:/var/named/named.loopback
启动DNS服务named:
[root@cp1 ~]# /etc/init.d/named start
Generating /etc/rndc.key: [确定]
启动 named: [确定]
测试1:正向解析
测试使用@127.0.0.1解析localhost:
[root@cp1 ~]# dig @127.0.0.1 localhost (如果现实没有此命令可安装 bind-utils)
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @127.0.0.1 localhost
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 11354
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1
;; QUESTION SECTION:
;localhost. IN A
;; ANSWER SECTION:
localhost. 86400 IN A 127.0.0.1
;; AUTHORITY SECTION:
localhost. 86400 IN NS localhost.
;; ADDITIONAL SECTION:
localhost. 86400 IN AAAA ::1
;; Query time: 0 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Mon Mar 13 22:31:29 2017
;; MSG SIZE rcvd: 85
测试使用@127.0.0.1解析localhost.localdomain:
[root@cp1 ~]# dig @127.0.0.1 localhost.localdomain
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @127.0.0.1 localhost.localdomain
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 26777
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1
;; QUESTION SECTION:
;localhost.localdomain. IN A
;; ANSWER SECTION:
localhost.localdomain. 86400 IN A 127.0.0.1
;; AUTHORITY SECTION:
localhost.localdomain. 86400 IN NS localhost.localdomain.
;; ADDITIONAL SECTION:
localhost.localdomain. 86400 IN AAAA ::1
;; Query time: 0 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Mon Mar 13 22:32:30 2017
;; MSG SIZE rcvd: 97
测试结果发现,将localhost和localhost.localdomain都解析到了127.0.0.1。
测试2:反向解析
反解析配置文件:/var/named/named.loopback
测试使用@127.0.0.1反解析127.0.0.1:
[root@cp1 ~]# dig @127.0.0.1 -x 127.0.0.1
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @127.0.0.1 -x 127.0.0.1
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 25857
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2
;; QUESTION SECTION:
;1.0.0.127.in-addr.arpa. IN PTR
;; ANSWER SECTION:
1.0.0.127.in-addr.arpa. 86400 IN PTR localhost.
;; AUTHORITY SECTION:
1.0.0.127.in-addr.arpa. 86400 IN NS 1.0.0.127.in-addr.arpa.
;; ADDITIONAL SECTION:
1.0.0.127.in-addr.arpa. 86400 IN A 127.0.0.1
1.0.0.127.in-addr.arpa. 86400 IN AAAA ::1
;; Query time: 0 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Mon Mar 13 22:33:43 2017
;; MSG SIZE rcvd: 121
测试结果发现,将127.0.0.1反解析到了localhost。
配置一个正向解析的域:123.com
编辑主配置文件:
[root@cp1 ~]# vim /etc/named.conf
在最后面添加一个域“123.com”,格式参照zone "."格式:
zone "123.com" IN {
type master;
file "123.com.zone";
};
检查主配置文件是否有错:
[root@cp1 ~]# named-checkconf
编辑123.com.zone文件:
[root@cp1 ~]# vim /var/named/123.com.zone
内容如下,格式参考/var/named/named.localhost:
$TTL 1D
@ IN SOA @ admin.123.com. (
2015010901 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
IN NS ns.123.com.
IN MX 5 mail.123.com.
mail IN A 192.168.1.60
ns IN A 192.168.1.60
www IN A 11.11.11.11
bbs IN CNAME www
检查域配置文件是否有错:
[root@cp1 ~]# named-checkzone "123.com" /var/named/123.com.zone
zone 123.com/IN: loaded serial 2015010901
OK
再次编辑主配置文件,
[root@cp1 ~]# vim /etc/named.conf
加入监听DNS的IP192.168.147.137
listen-on port 53 { 127.0.0.1;192.168.147.137; };
重启:
[root@cp1 ~]# /etc/init.d/named restart
停止 named:. [确定]
启动 named: [确定]
测试1:解析www.123.com:
[root@cp1 ~]# dig @192.168.147.137 www.123.com
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @192.168.147.137 www.123.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 31526
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1
;; QUESTION SECTION:
;www.123.com. IN A
;; ANSWER SECTION:
www.123.com. 86400 IN A 11.11.11.11
;; AUTHORITY SECTION:
123.com. 86400 IN NS ns.123.com.
;; ADDITIONAL SECTION:
ns.123.com. 86400 IN A 192.168.134.128
;; Query time: 15 msec
;; SERVER: 192.168.147.137#53(192.168.147.137)
;; WHEN: Mon Mar 13 23:37:22 2017
;; MSG SIZE rcvd: 78
测试2:解析bbs.123.com:
[root@cp1 ~]# dig @192.168.147.137 bbs.123.com
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @192.168.147.137 bbs.123.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 9966
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 1, ADDITIONAL: 1
;; QUESTION SECTION:
;bbs.123.com. IN A
;; ANSWER SECTION:
bbs.123.com. 86400 IN CNAME www.123.com.
www.123.com. 86400 IN A 11.11.11.11
;; AUTHORITY SECTION:
123.com. 86400 IN NS ns.123.com.
;; ADDITIONAL SECTION:
ns.123.com. 86400 IN A 192.168.134.128
;; Query time: 1 msec
;; SERVER: 192.168.147.137#53(192.168.147.137)
;; WHEN: Mon Mar 13 23:38:53 2017
;; MSG SIZE rcvd: 96
测试3:mail.123.com:
[root@cp1 ~]# dig @192.168.147.137 mail.123.com
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @192.168.147.137 mail.123.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 41160
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1
;; QUESTION SECTION:
;mail.123.com. IN A
;; ANSWER SECTION:
mail.123.com. 86400 IN A 192.168.134.129
;; AUTHORITY SECTION:
123.com. 86400 IN NS ns.123.com.
;; ADDITIONAL SECTION:
ns.123.com. 86400 IN A 192.168.134.128
;; Query time: 0 msec
;; SERVER: 192.168.147.137#53(192.168.147.137)
;; WHEN: Mon Mar 13 23:39:42 2017
;; MSG SIZE rcvd: 79
测试4:没有配置的mail2解析失败
[root@cp1 ~]# dig @192.168.147.137 mail2.123.com
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @192.168.147.137 mail2.123.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 47121
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 0
;; QUESTION SECTION:
;mail2.123.com. IN A
;; AUTHORITY SECTION:
123.com. 10800 IN SOA 123.com. admin.123.com. 2015010901 86400 3600 604800 10800
;; Query time: 9 msec
;; SERVER: 192.168.147.137#53(192.168.147.137)
;; WHEN: Mon Mar 13 23:40:34 2017
;; MSG SIZE rcvd: 73
配置一个反向解析的域:147.168.192.zone
(反解析一般用于企业的邮件服务器,能够反解析出我的域名的IP我才给你发邮件)
编辑主配置文件:
[root@cp1 ~]# vim /etc/named.conf
在最后面添加一个域:
zone "147.168.192.in-addr.arpa" IN {
type master;
file "147.168.192.zone";
};
检查主配置文件是否有错:
[root@cp1 ~]# named-checkconf
编辑对应的zone文件:
[root@cp1 ~]# vim /var/named/147.168.192.zone
$TTL 1D
@ IN SOA @ admin.123.com. (
2015010901 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
IN NS ns.123.com.
137 IN PTR ns.123.com.
138 IN PTR mail.123.com.
检查域配置文件是否有错:
[root@cp1 ~]# named-checkzone "147.168.192" /var/named/147.168.192.zone
zone 147.168.192/IN: loaded serial 2015010901
OK
重启:
[root@cp1 ~]# /etc/init.d/named restart
停止 named:. [确定]
启动 named: [确定]
测试1:DNS服务器自身IP反解析成功
[root@cp1 ~]# dig @192.168.147.137 -x 192.168.147.137
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @192.168.147.137 -x 192.168.147.137
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 38679
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1
;; QUESTION SECTION:
;137.147.168.192.in-addr.arpa. IN PTR
;; ANSWER SECTION:
137.147.168.192.in-addr.arpa. 86400 IN PTR ns.123.com.
;; AUTHORITY SECTION:
147.168.192.in-addr.arpa. 86400 IN NS ns.123.com.
;; ADDITIONAL SECTION:
ns.123.com. 86400 IN A 192.168.134.128
;; Query time: 0 msec
;; SERVER: 192.168.147.137#53(192.168.147.137)
;; WHEN: Tue Mar 14 00:00:02 2017
;; MSG SIZE rcvd: 100
测试2:域192.168.147内的任意主机都能反解析成功
[root@cp1 ~]# dig @192.168.147.137 -x 192.168.147.138
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @192.168.147.137 -x 192.168.147.138
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 50957
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1
;; QUESTION SECTION:
;138.147.168.192.in-addr.arpa. IN PTR
;; ANSWER SECTION:
138.147.168.192.in-addr.arpa. 86400 IN PTR mail.123.com.
;; AUTHORITY SECTION:
147.168.192.in-addr.arpa. 86400 IN NS ns.123.com.
;; ADDITIONAL SECTION:
ns.123.com. 86400 IN A 192.168.134.128
;; Query time: 0 msec
;; SERVER: 192.168.147.137#53(192.168.147.137)
;; WHEN: Tue Mar 14 00:01:31 2017
;; MSG SIZE rcvd: 105
测试3:不在域192.168.147内的IP反解析失败:
[root@cp1 ~]# dig @192.168.147.137 -x 192.168.123.138
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @192.168.147.137 -x 192.168.123.138
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 37175
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;138.123.168.192.in-addr.arpa. IN PTR
;; Query time: 1240 msec
;; SERVER: 192.168.147.137#53(192.168.147.137)
;; WHEN: Tue Mar 14 00:01:58 2017
;; MSG SIZE rcvd: 46
dns服务器主从配置:
主DNS服务器:192.168.147.137
从DNS服务器:192.168.147.138
在从DNS服务器上192.168.147.138:
安装DNS:
[root@cp2 ~]# yum install -y bind
编辑主配置:
[root@cp2 ~]# vim /etc/named.conf
注释掉以下两行,表示监听所有IP
// listen-on port 53 { 127.0.0.1; };
// listen-on-v6 port 53 { ::1; };
在最后面添加与主DNS一样的域配置,稍作修改如下:
zone "123.com" IN {
type slave;
file "slaves/123.com.zone";
masters { 192.168.147.137; };
};
zone "147.168.192.in-addr.arpa" IN {
type slave;
file "slaves/147.168.192.zone";
masters { 192.168.147.137; };
};
检查主配置文件是否有错:
[root@cp2 ~]# named-checkconf
启动:
[root@cp2 ~]# /etc/init.d/named start
Generating /etc/rndc.key: [确定]
启动 named: [确定]
查看生成的文件:
[root@cp2 ~]# ls /var/named/slaves/
123.com.zone 147.168.192.zone
查看123.com.zone内容(可以看到在主DNS上的配置被同步到从DNS上):
[root@cp2 ~]# cat /var/named/slaves/123.com.zone
$ORIGIN .
$TTL 86400 ; 1 day
123.com IN SOA 123.com. admin.123.com. (
2015010901 ; serial
86400 ; refresh (1 day)
3600 ; retry (1 hour)
604800 ; expire (1 week)
10800 ; minimum (3 hours)
)
NS ns.123.com.
MX 5 mail.123.com.
$ORIGIN 123.com.
bbs CNAME www
mail A 192.168.134.129
ns A 192.168.134.128
www A 11.11.11.11
测试从DNS解析www.123.com:
[root@cp2 ~]# dig @192.168.147.138 www.123.com
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @192.168.147.138 www.123.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 38327
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1
;; QUESTION SECTION:
;www.123.com. IN A
;; ANSWER SECTION:
www.123.com. 86400 IN A 11.11.11.11
;; AUTHORITY SECTION:
123.com. 86400 IN NS ns.123.com.
;; ADDITIONAL SECTION:
ns.123.com. 86400 IN A 192.168.134.128
;; Query time: 1 msec
;; SERVER: 192.168.147.138#53(192.168.147.138)
;; WHEN: Tue Mar 14 00:34:43 2017
;; MSG SIZE rcvd: 78
测试从DNSbbs:
[root@cp2 ~]# dig @192.168.147.138 bbs.123.com
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @192.168.147.138 bbs.123.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 36960
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 1, ADDITIONAL: 1
;; QUESTION SECTION:
;bbs.123.com. IN A
;; ANSWER SECTION:
bbs.123.com. 86400 IN CNAME www.123.com.
www.123.com. 86400 IN A 11.11.11.11
;; AUTHORITY SECTION:
123.com. 86400 IN NS ns.123.com.
;; ADDITIONAL SECTION:
ns.123.com. 86400 IN A 192.168.134.128
;; Query time: 0 msec
;; SERVER: 192.168.147.138#53(192.168.147.138)
;; WHEN: Tue Mar 14 00:46:35 2017
;; MSG SIZE rcvd: 96
测试反解析:
[root@cp2 ~]# dig @192.168.147.138 -x 192.168.147.137
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @192.168.147.138 -x 192.168.147.137
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 5809
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1
;; QUESTION SECTION:
;137.147.168.192.in-addr.arpa. IN PTR
;; ANSWER SECTION:
137.147.168.192.in-addr.arpa. 86400 IN PTR ns.123.com.
;; AUTHORITY SECTION:
147.168.192.in-addr.arpa. 86400 IN NS ns.123.com.
;; ADDITIONAL SECTION:
ns.123.com. 86400 IN A 192.168.134.128
;; Query time: 0 msec
;; SERVER: 192.168.147.138#53(192.168.147.138)
;; WHEN: Tue Mar 14 00:48:28 2017
;; MSG SIZE rcvd: 100
测试结果发现,从DNS服务器正常工作。
在主上增加一条记录:
[root@cp1 ~]# vim /var/named/123.com.zone
$TTL 1D
@ IN SOA @ admin.123.com. (
2015010902 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
IN NS ns.123.com.
IN MX 5 mail.123.com.
mail IN A 192.168.147.137
ns IN A 192.168.147.138
www IN A 11.11.11.11
bbs IN CNAME www
test IN A 111.111.111.111
重启:
[root@cp1 ~]# /etc/init.d/named restart
停止 named:. [确定]
启动 named: [确定]
测试解析新加入的记录 test.123.com:
[root@cp1 ~]# dig @192.168.147.137 test.123.com
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @192.168.147.137 test.123.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 2695
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1
;; QUESTION SECTION:
;test.123.com. IN A
;; ANSWER SECTION:
test.123.com. 86400 IN A 111.111.111.111
;; AUTHORITY SECTION:
123.com. 86400 IN NS ns.123.com.
;; ADDITIONAL SECTION:
ns.123.com. 86400 IN A 192.168.147.138
;; Query time: 0 msec
;; SERVER: 192.168.147.137#53(192.168.147.137)
;; WHEN: Tue Mar 14 00:53:47 2017
;; MSG SIZE rcvd: 79
1天刷新一次不方便测试,我们想只要主发生更改,从立即跟着更改:
在主上编辑配置文件:加入向从发送通知的配置
zone "123.com" IN {
type master;
file "123.com.zone";
notify yes;
also-notify { 192.168.147.138; };
};
zone "147.168.192.in-addr.arpa" IN {
type master;
file "147.168.192.zone";
notify yes;
also-notify { 192.168.147.138; };
};
检查配置:
[root@cp1 ~]# named-checkconf
重启:[root@cp1 ~]# /etc/init.d/named restart
停止 named:. [确定]
启动 named: [确定]
在从上测试:
发现从DNS上配置文件123.com.zone也自动更新:
[root@cp2 ~]# cat /var/named/slaves/123.com.zone
$ORIGIN .
$TTL 86400 ; 1 day
123.com IN SOA 123.com. admin.123.com. (
2015010902 ; serial
86400 ; refresh (1 day)
3600 ; retry (1 hour)
604800 ; expire (1 week)
10800 ; minimum (3 hours)
)
NS ns.123.com.
MX 5 mail.123.com.
$ORIGIN 123.com.
bbs CNAME www
mail A 192.168.147.137
ns A 192.168.147.138
test A 111.111.111.111
www A 11.11.11.11
测试解析 test.123.com:
[root@cp2 ~]# dig @192.168.147.138 test.123.com
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6_8.4 <<>> @192.168.147.138 test.123.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 57454
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1
;; QUESTION SECTION:
;test.123.com. IN A
;; ANSWER SECTION:
test.123.com. 86400 IN A 111.111.111.111
;; AUTHORITY SECTION:
123.com. 86400 IN NS ns.123.com.
;; ADDITIONAL SECTION:
ns.123.com. 86400 IN A 192.168.147.138
;; Query time: 0 msec
;; SERVER: 192.168.147.138#53(192.168.147.138)
;; WHEN: Tue Mar 14 00:58:05 2017
;; MSG SIZE rcvd: 79
本文出自 “12350027” 博客,谢绝转载!
DNS配置安装和DNS主从配置
