首页 > 代码库 > LVS/DR模型及持久连接
LVS/DR模型及持久连接
| HostName | AddressIP | Role | VirtualIP DEV |
| LVS/DR | 192.168.1.150/24 | LVS,CA | eth0:0 192.168.1.250 |
| node2 | 192.168.1.120/24 | RealServer(httpd) | lo:0 192.168.1.250 |
| node3 | 192.168.1.130/24 | RealServer(httpd) | lo:0 192.168.1.250 |
1)DR模型配置前的准备
两RealServer配置如下(一摸一样):
[root@node2 ~]# echo 1 > /proc/sys/net/ipv4/conf/lo/arp_ignore [root@node2 ~]# echo 1 > /proc/sys/net/ipv4/conf/all/arp_ignore [root@node2 ~]# echo 2 > /proc/sys/net/ipv4/conf/lo/arp_announce [root@node2 ~]# echo 2 > /proc/sys/net/ipv4/conf/all/arp_announce [root@node2 ~]# ifconfig lo:0 192.168.1.250 broadcast 192.168.1.250 netmask 255.255.255.255 up [root@node2 ~]# route add -host 192.168.1.250 dev lo:0 [root@node2 ~]# ifconfig lo:0 lo:0 Link encap:Local Loopback inet addr:192.168.1.250 Mask:255.255.255.255 UP LOOPBACK RUNNING MTU:16436 Metric:1
LVS/DR配置
[root@LVS/DR ~]# ifconfig eth0:0 192.168.1.250 broadcast 192.168.1.250 netmask 255.255.255.255 up [root@LVS/DR ~]# route add -host 192.168.1.250 dev eth0:0
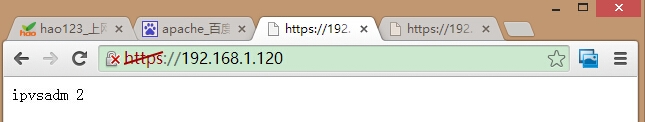
2)Apache安装好了验证是否能够访问(安装过程略)
[root@LVS/DR ~]# curl 192.168.1.120 ipvsadm 2 [root@LVS/DR ~]# curl 192.168.1.130 ipvsadm 3
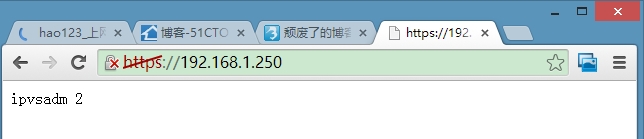
3)创建负载均衡群集
[root@LVS/DR ~]# ipvsadm -A -t 192.168.1.250:80 -s rr [root@LVS/DR ~]# ipvsadm -a -t 192.168.1.250:80 -r 192.168.1.120 -g [root@LVS/DR ~]# ipvsadm -a -t 192.168.1.250:80 -r 192.168.1.130 -g [root@LVS/DR ~]# ipvsadm -L -n IP Virtual Server version 1.2.1 (size=4096) Prot LocalAddress:Port Scheduler Flags -> RemoteAddress:Port Forward Weight ActiveConn InActConn TCP 192.168.1.250:80 rr -> 192.168.1.120:80 Route 1 0 0 -> 192.168.1.130:80 Route 1 0 0
验证群集是否配置成功
![B]7J4]R[90G%F)957]4`[$0.jpg wKiom1Rxe67AyE_2AAB_ehF0HN8555.jpg](http://s3.51cto.com/wyfs02/M02/53/D2/wKiom1Rxe67AyE_2AAB_ehF0HN8555.jpg)
到此一个简单的DR模型就配置成功了
配置持久连接这里我们将80,443端口绑定在一起这就会用mangle搭上一个标记
5)安装mod_ssl模块
[root@node3 ~]# yum install mod_ssl
6)申请证书
1 创建CA证书颁发机构 [root@LVS/DR CA]# (umask 077;openssl genrsa 1024 > private/cakey.pem) 创建私钥 Generating RSA private key, 1024 bit long modulus .................................++++++ ..................................++++++ e is 65537 (0x10001) 自签证书 [root@LVS/DR CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 365 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.‘, the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:CQ Locality Name (eg, city) [Default City]:chongqing Organization Name (eg, company) [Default Company Ltd]:MT Organizational Unit Name (eg, section) []:teach Common Name (eg, your name or your server‘s hostname) []:ca.mictiger.com Email Address []: [root@LVS/DR CA]# ls cacert.pem certs crl newcerts private [root@LVS/DR CA]# touch index.txt [root@LVS/DR CA]# touch serial [root@LVS/DR CA]# echo 01 > serial 2 RealServer生成证书签署请求 生成私钥 [root@node3 conf]# mkdir ssl [root@node3 ssl]# (umask 077;openssl genrsa 1024 > apache.key) Generating RSA private key, 1024 bit long modulus ................++++++ ....++++++ e is 65537 (0x10001) 证书签署请求 [root@node3 ssl]# openssl req -new -key apache.key -out apache.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.‘, the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:CQ Locality Name (eg, city) [Default City]:chongqing Organization Name (eg, company) [Default Company Ltd]:MT Organizational Unit Name (eg, section) []:teach Common Name (eg, your name or your server‘s hostname) []:192.168.1.250 Email Address []: Please enter the following ‘extra‘ attributes to be sent with your certificate request A challenge password []: An optional company name []: scp apache.csr root@192.168.1.150:/tmp 3 CA签署证书 [root@LVS/DR tmp]# openssl ca -in apache.csr -out apache.crt -days 365 Using configuration from /etc/pki/tls/openssl.cnf Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Nov 23 04:53:26 2014 GMT Not After : Nov 23 04:53:26 2015 GMT Subject: countryName = CN stateOrProvinceName = CQ organizationName = MT organizationalUnitName = teach commonName = 192.168.1.250 X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 22:5E:3C:6D:27:5A:94:9A:E7:F2:35:0F:76:5A:C0:D6:80:1F:E7:8E X509v3 Authority Key Identifier: keyid:CD:4E:2E:C5:F7:BF:B3:6F:5E:23:C7:FB:A6:3B:52:71:6C:70:3A:90 Certificate is to be certified until Nov 23 04:53:26 2015 GMT (365 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated [root@LVS/DR tmp]# scp apache.crt root@192.168.1.130:/etc/httpd/conf/ssl apache.crt 100% 3047 3.0KB/s 00:00 4 配置Apache的https服务 /etc/httpd/conf.d/ssl.conf 配置如下几个选项 DocumentRoot "/var/www/html" SSLCertificateFile /etc/httpd/conf/ssl/apache.crt SSLCertificateKeyFile /etc/httpd/conf/ssl/apache.key 5 copy node3的ssl配置到node2并重启httpd服务 [root@node3 httpd]# scp conf.d/ssl.conf root@192.168.1.120:/etc/httpd/conf.d [root@node3 httpd]# scp -rp conf/ssl/ root@192.168.1.120:/etc/httpd/conf/ssl/
验证https服务是否配置成功
![NWY0ZK_53]AVBQIXLC@}A$I.jpg wKiom1Rxg4KSFkfRAACgfL6J11o319.jpg](http://s3.51cto.com/wyfs02/M01/53/D2/wKiom1Rxg4KSFkfRAACgfL6J11o319.jpg)
7)配置iptables和ipvsadm
mangle表 [root@LVS/DR ~]# iptables -t mangle -A PREROUTING -d 192.168.1.250 -p tcp --dport 80 -j MARK --set-mark 80 [root@LVS/DR ~]# iptables -t mangle -A PREROUTING -d 192.168.1.250 -p tcp --dport 443 -j MARK --set-mark 80 定义群集 root@LVS/DR ~]# ipvsadm -A -f 80 -s rr -p [root@LVS/DR ~]# ipvsadm -a -f 80 -r 192.168.1.130 -g [root@LVS/DR ~]# ipvsadm -a -f 80 -r 192.168.1.120 -g [root@LVS/DR ~]# ipvsadm -Ln IP Virtual Server version 1.2.1 (size=4096) Prot LocalAddress:Port Scheduler Flags -> RemoteAddress:Port Forward Weight ActiveConn InActConn FWM 80 rr persistent 360 -> 192.168.1.120:0 Route 1 0 0 -> 192.168.1.130:0 Route 1 0 0
本文出自 “LoveFish” 博客,请务必保留此出处http://mictiger.blog.51cto.com/4854014/1581641
LVS/DR模型及持久连接
声明:以上内容来自用户投稿及互联网公开渠道收集整理发布,本网站不拥有所有权,未作人工编辑处理,也不承担相关法律责任,若内容有误或涉及侵权可进行投诉: 投诉/举报 工作人员会在5个工作日内联系你,一经查实,本站将立刻删除涉嫌侵权内容。
