首页 > 代码库 > 个人博客http转https
个人博客http转https
搭建个人博客的时候,就看过一些免费证书申请的文章,也浏览过一些使用Https的博客。使用Https要比Http安全很多,至少在国内很普通的流量劫持攻击会减少很多。闲来无事,测试把自己的个人博客也升级到Https。
使用Https加密首先就需要申请个人博客证书,收费的证书颁发机构国内和国外都有很多。个人博客推荐使用现在比较流行的Let‘s Encrypt。申请过程比较简单,使用官方自动化脚本:
1、配置git环境:# yum install git
2、下载自动化脚本到本地
# git clone https://github.com/certbot/certbot
# cd certbot
3、生成证书
./certbot-auto certonly --standalone --email loryxxx@hotmail.com -d iorisun.com -d www.iorisun.com
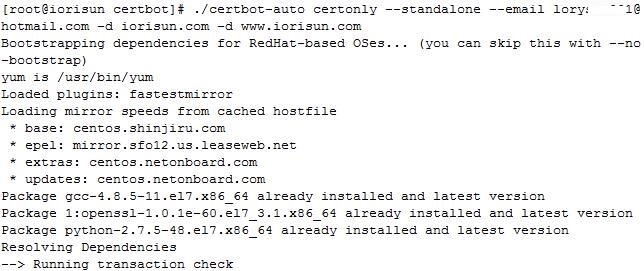
将安装以下软件包
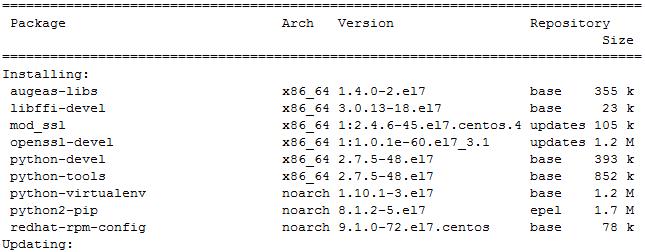
安装过程,需要手动确认是否安装,输入Y确认。另外还需要接受官方协议,输入A回车即可。
注意:申请时,防火墙需要开通https端口
# firewall-cmd --permanent --zone=public --add-service=https
# firewall-cmd --reload
申请成功后,有以下提示:

可通过tree命令查看:# tree /etc/letsencrypt/live/
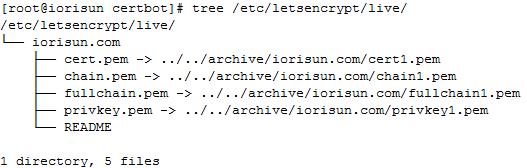
4、修改nginx配置文件
# vim /etc/nginx/conf.d/default.conf
在Nginx配置文件中加入SSL参数定义,把http重定向到https
如下:修改和增加以下内容
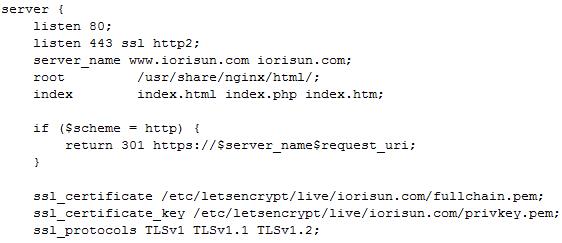
重启服务后,再打开网站就可以看到绿色的小锁了。
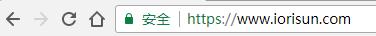
5、设置证书自动延期
Let‘s Encrypt的证书有效期只有90天,需要定期更新证书:
通过crontab制定一个计划任务,每2个月更新一次。
* * * 2 * root /root/certbot/certbot-auto renew --standalone --pre-hook "service nginx stop" --post-hook "service nginx start" --force-renewal
或者使用./certbot-auto renew -v命令也可以。
6、修改博客站点地址
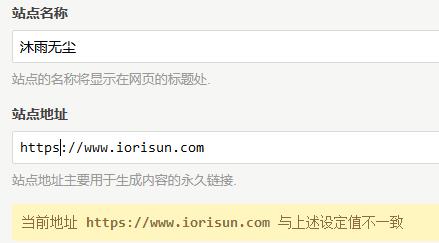
优化Https安全性:
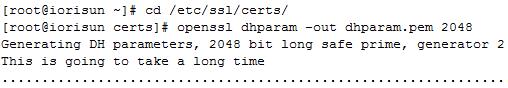
1、生成dhparam.pem
# cd /etc/ssl/certs/
# openssl dhparam -out dhparam.pem 2048
2、生成HTTP Public Key Pinning
# cd /etc/letsencrypt/live/iorisun.com/
# openssl rsa -in privkey.pem -outform der -pubout | openssl dgst -sha256 -binary | openssl enc -base64
writing RSA key
9rcncxVnzws62MPkX5nUJPKs5jAGAhnxeqANv0Hx7Vo=
# openssl x509 -in chain.pem -pubkey -noout | openssl rsa -pubin -outform der | openssl dgst -sha256 -binary | openssl enc -base64
writing RSA key
YLh1dUR9y6Kja30RrAn7JKnbQG/uEtLMkBgFF2Fuihg=
3、修改nginx配置文件:
# vim /etc/nginx/conf.d/default.conf
server {
listen 80;
listen 443 ssl http2;
server_name www.iorisun.com iorisun.com;
root /usr/share/nginx/html/;
index index.html index.php index.htm;
if ($scheme = http) {
return 301 https://$server_name$request_uri;
}
ssl_certificate /etc/letsencrypt/live/iorisun.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/iorisun.com/privkey.pem;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers "ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4";
ssl_prefer_server_ciphers on;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
ssl_session_tickets off;
ssl_stapling on;
ssl_stapling_verify on;
ssl_trusted_certificate /etc/letsencrypt/live/iorisun.com/chain.pem;
ssl_dhparam /etc/ssl/certs/dhparam.pem;
server_tokens off;
resolver 8.8.4.4 8.8.8.8 valid=300s;
resolver_timeout 10s;
fastcgi_hide_header X-Powered-By;
add_header Strict-Transport-Security "max-age=63072000; includeSubDomains; preload";
add_header Public-Key-Pins ‘pin-sha256="9rcncxVnzws62MPkX5nUJPKs5jAGAhnxeqANv0Hx7Vo="; pin-sha256="YLh1dUR9y6Kja30RrAn7JKnbQG/uEtLMkBgFF2Fuihg="; max-age=2592000; includeSubDomains‘ always;
add_header X-Frame-Options DENY;
add_header X-Content-Type-Options nosniff; 配置完之后可以测试一下网站的安全级别:https://www.ssllabs.com/ssltest/
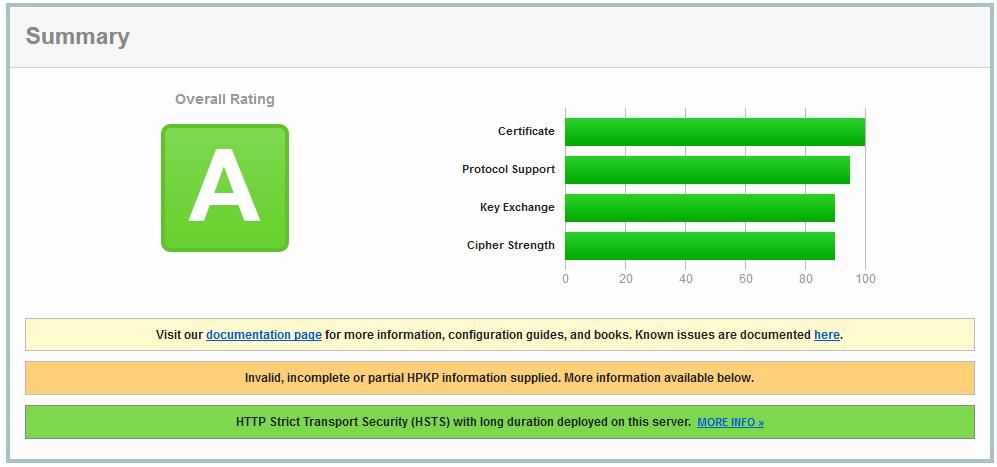
个人博客http转https
