首页 > 代码库 > Tomcat基础配置(2)-Tomcat连接器
Tomcat基础配置(2)-Tomcat连接器
接上篇博客:http://sohudrgon.blog.51cto.com/3088108/1604989
实验架构图:
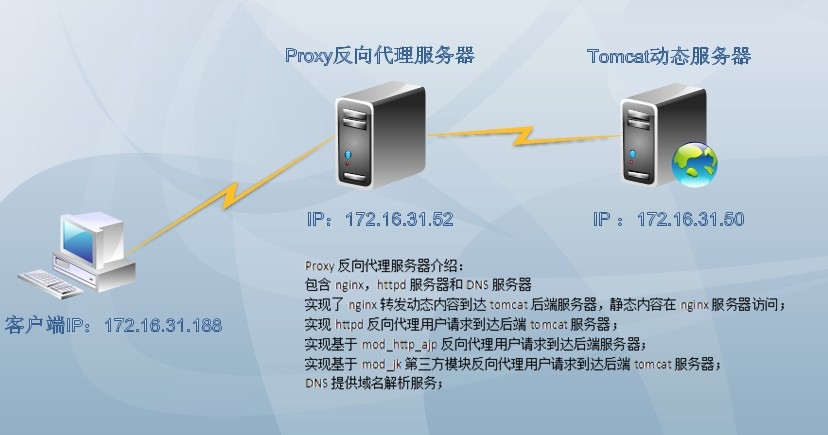
实验说明:
1.用户请求到达反向代理服务器,反向代理服务器将用户请求转发到后端tomcat服务器;
2.Proxy反向代理服务器介绍:
包含nginx,httpd服务器和DNS服务器
实现了nginx转发动态内容到达tomcat后端服务器,静态内容在nginx服务器访问;
实现httpd反向代理用户请求到达后端tomcat服务器;
实现基于mod_http_ajp反向代理用户请求到达后端服务器;
实现基于mod_jk第三方模块反向代理用户请求到达后端tomcat服务器;
DNS提供域名解析服务;DNS的构建参考包括:http://sohudrgon.blog.51cto.com/3088108/1588344
实验实现
Tomcat连接器介绍:
Tomcat的连接器分为两类:HTTP连接器和Web服务器连接器。
Tomcat的HTTP连接器有三种:
1) 基于java的HTTP/1.1连接器,这也是Tomcat6默认使用的连接器,即Coyote;它是Tomcat作为standalone模式工作时所用到的连接器,可直接响应来自用户浏览器的关于JSP、servlet和HTML的请求;此连接器是一个Java类,定义在server.xml当中,默认使用8080端口;
2) Java开发的高性能NIO HTTP/1.1连接器,它支持非阻塞式IO和Comnet,在基于库向tomcat发起请求时,此连接器表现不俗;但其实现不太成熟,有严重bug存在;
3) C/C++开发的native APR HTTP/1.1连接器;在负载较大的场景中,此连接器可以提供非常好的性能;APR即Apache Portable Runtime,它是一个能让开发者采用与平台无关的风格的方式来开发C/C++代码本地库,它能够很好的跨Windows,
4)AJP(Apache JServ Protocol):
AJP是面向数据包的基于TCP/IP的协议,它在Apache和Tomcat的实例之间提供了一个专用的通信信道。目前常用AJP协议的版本是1.3,它主要有以下特征:
1) 在快速网络有着较好的性能表现,支持数据压缩传输;
2) 支持SSL,加密及客户端证书;
3) 支持Tomcat实例集群;
4) 支持在apache和tomcat之间的连接的重用;
Apache可以通过mod_jk和mod_proxy模块跟Tomcat整合,但mod_proxy只有在apache 2.2.x系列的版本才直接提供,但它可以提供更丰富的功能和安全性;而对于apache 1.3.x和2.0.x来说mod_jk才更适用。
一.配置apache通过mod_proxy模块与Tomcat连接:
1、检测当前的apache是否支持mod_proxy、mod_proxy_http、mod_proxy_ajp和proxy_balancer_module模块:
# httpd -M …………………… proxy_module (shared) proxy_balancer_module (shared) proxy_ftp_module (shared) proxy_http_module (shared) proxy_ajp_module (shared) proxy_connect_module (shared) ……………………
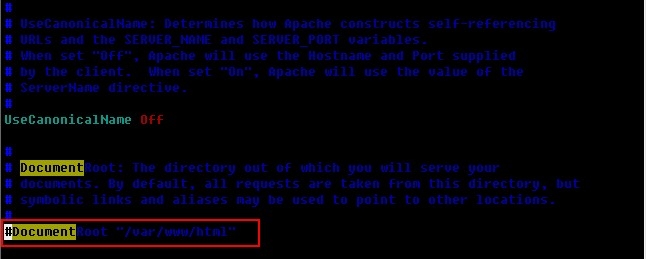
2、在httpd.conf的全局配置段或虚拟主机中添加如下内容:
[root@proxy ~]# vim /etc/httpd/conf/httpd.conf #注释掉如下内容 #DocumentRoot "/var/www/html"
3.创建虚拟主机配置文件:
[root@proxy ~]# vim /etc/httpd/conf.d/mod_proxy_http.conf NameVirtualHost *:80 <VirtualHost *:80> ServerName www1.stu31.com ProxyVia on ProxyRequests off ProxyPreserveHost on <proxy *> Order deny,all Allow from all </proxy> ProxyPass / http://172.16.31.50:80/ ProxyPassReverse / http://172.16.31.50:80/ <location /> Order deny,allow Allow from all </location> </VirtualHost>
将到达httpd服务器的所有请求转发到后端Tomcat服务器;
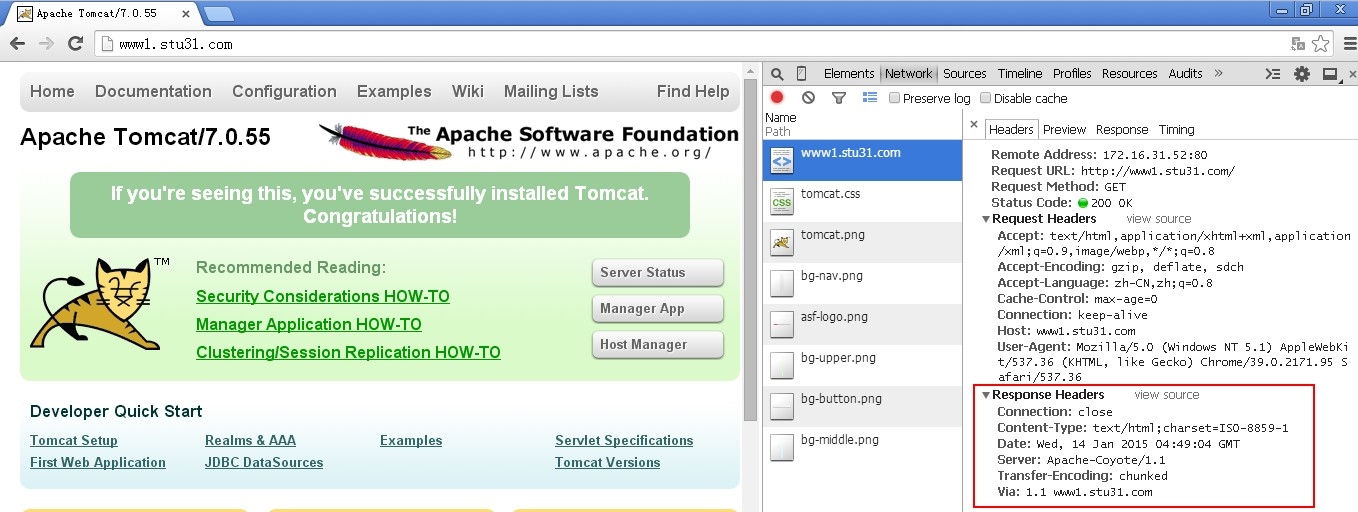
4.重启服务访问测试:
[root@proxy ~]# service httpd start
5.抓取tomcat服务器的80端口的报文
[root@tom1 tomcat]# tcpdump -nn -i eth0 port 80 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 12:50:04.764070 IP 172.16.31.52.34502 > 172.16.31.50.80: Flags [F.], seq 1440588809, ack 2024396504, win 638, options [nop,nop,TS val 33968077 ecr 47822538], length 0 12:50:04.764089 IP 172.16.31.50.80 > 172.16.31.52.34502: Flags [.], ack 1, win 261, options [nop,nop,TS val 47862785 ecr 33968077], length 0 12:50:04.764837 IP 172.16.31.52.34512 > 172.16.31.50.80: Flags [S], seq 1275354295, win 14600, options [mss 1460,sackOK,TS val 33968078 ecr 0,nop,wscale 5], length 0 12:50:04.764853 IP 172.16.31.50.80 > 172.16.31.52.34512: Flags [S.], seq 1466947168, ack 1275354296, win 14480, options [mss 1460,sackOK,TS val 47862786 ecr 33968078,nop,wscale 6], length 0 12:50:04.765678 IP 172.16.31.52.34512 > 172.16.31.50.80: Flags [.], ack 1, win 457, options [nop,nop,TS val 33968078 ecr 47862786], length 0 12:50:04.765700 IP 172.16.31.52.34512 > 172.16.31.50.80: Flags [P.], seq 1:488, ack 1, win 457, options [nop,nop,TS val 33968079 ecr 47862786], length 487 12:50:04.765706 IP 172.16.31.50.80 > 172.16.31.52.34512: Flags [.], ack 488, win 243, options [nop,nop,TS val 47862786 ecr 33968079], length 0 12:50:04.768922 IP 172.16.31.50.80 > 172.16.31.52.34512: Flags [.], seq 1:2897, ack 488, win 243, options [nop,nop,TS val 47862790 ecr 33968079], length 2896 12:50:04.769059 IP 172.16.31.50.80 > 172.16.31.52.34512: Flags [.], seq 2897:5793, ack 488, win 243, options [nop,nop,TS val 47862790 ecr 33968079], length 2896 12:50:04.769152 IP 172.16.31.50.80 > 172.16.31.52.34512: Flags [P.], seq 5793:8689, ack 488, win 243, options [nop,nop,TS val 47862790 ecr 33968079], length 2896 12:50:04.769239 IP 172.16.31.50.80 > 172.16.31.52.34512: Flags [P.], seq 8689:9001, ack 488, win 243, options [nop,nop,TS val 47862790 ecr 33968079], length 312 12:50:04.769360 IP 172.16.31.50.80 > 172.16.31.52.34512: Flags [.], seq 9001:10449, ack 488, win 243, options [nop,nop,TS val 47862790 ecr 33968079], length 1448 12:50:04.772472 IP 172.16.31.52.34512 > 172.16.31.50.80: Flags [.], ack 8689, win 547, options [nop,nop,TS val 33968082 ecr 47862790], length 0 12:50:04.772502 IP 172.16.31.52.34512 > 172.16.31.50.80: Flags [.], ack 9001, win 638, options [nop,nop,TS val 33968082 ecr 47862790], length 0 12:50:04.772519 IP 172.16.31.52.34512 > 172.16.31.50.80: Flags [.], ack 10449, win 728, options [nop,nop,TS val 33968083 ecr 47862790], length 0 12:50:04.772589 IP 172.16.31.50.80 > 172.16.31.52.34512: Flags [P.], seq 10449:11373, ack 488, win 243, options [nop,nop,TS val 47862793 ecr 33968079], length 924 12:50:04.778834 IP 172.16.31.52.34512 > 172.16.31.50.80: Flags [.], ack 11373, win 819, options [nop,nop,TS val 33968092 ecr 47862793], length 0 12:50:04.879351 IP 172.16.31.52.34503 > 172.16.31.50.80: Flags [F.], seq 3040554536, ack 2056466676, win 547, options [nop,nop,TS val 33968193 ecr 47822537], length 0 12:50:04.879375 IP 172.16.31.50.80 > 172.16.31.52.34503: Flags [.], ack 1, win 261, options [nop,nop,TS val 47862900 ecr 33968193], length 0 12:50:04.879401 IP 172.16.31.52.34513 > 172.16.31.50.80: Flags [S], seq 1653528953, win 14600, options [mss 1460,sackOK,TS val 33968193 ecr 0,nop,wscale 5], length 0 12:50:04.879414 IP 172.16.31.50.80 > 172.16.31.52.34513: Flags [S.], seq 974646591, ack 1653528954, win 14480, options [mss 1460,sackOK,TS val 47862900 ecr 33968193,nop,wscale 6], length 0 12:50:04.883263 IP 172.16.31.52.34513 > 172.16.31.50.80: Flags [.], ack 1, win 457, options [nop,nop,TS val 33968197 ecr 47862900], length 0 12:50:04.883296 IP 172.16.31.52.34513 > 172.16.31.50.80: Flags [P.], seq 1:564, ack 1, win 457, options [nop,nop,TS val 33968197 ecr 47862900], length 563 12:50:04.883306 IP 172.16.31.50.80 > 172.16.31.52.34513: Flags [.], ack 564, win 244, options [nop,nop,TS val 47862904 ecr 33968197], length 0 12:50:04.884890 IP 172.16.31.50.80 > 172.16.31.52.34513: Flags [P.], seq 1:124, ack 564, win 244, options [nop,nop,TS val 47862906 ecr 33968197], length 123 12:50:04.885858 IP 172.16.31.52.34507 > 172.16.31.50.80: Flags [F.], seq 1358967460, ack 712877484, win 457, options [nop,nop,TS val 33968200 ecr 47810634], length 0 12:50:04.885875 IP 172.16.31.50.80 > 172.16.31.52.34507: Flags [.], ack 1, win 244, options [nop,nop,TS val 47862907 ecr 33968200], length 0 12:50:04.885900 IP 172.16.31.52.34514 > 172.16.31.50.80: Flags [S], seq 2770143655, win 14600, options [mss 1460,sackOK,TS val 33968200 ecr 0,nop,wscale 5], length 0 12:50:04.885912 IP 172.16.31.50.80 > 172.16.31.52.34514: Flags [S.], seq 464845932, ack 2770143656, win 14480, options [mss 1460,sackOK,TS val 47862907 ecr 33968200,nop,wscale 6], length 0 12:50:04.885931 IP 172.16.31.52.34513 > 172.16.31.50.80: Flags [.], ack 124, win 457, options [nop,nop,TS val 33968200 ecr 47862906], length 0 12:50:04.886116 IP 172.16.31.52.34514 > 172.16.31.50.80: Flags [.], ack 1, win 457, options [nop,nop,TS val 33968200 ecr 47862907], length 0 12:50:04.888681 IP 172.16.31.52.34514 > 172.16.31.50.80: Flags [P.], seq 1:566, ack 1, win 457, options [nop,nop,TS val 33968201 ecr 47862907], length 565 12:50:04.888721 IP 172.16.31.50.80 > 172.16.31.52.34514: Flags [.], ack 566, win 244, options [nop,nop,TS val 47862909 ecr 33968201], length 0 12:50:04.889921 IP 172.16.31.50.80 > 172.16.31.52.34514: Flags [P.], seq 1:124, ack 566, win 244, options [nop,nop,TS val 47862911 ecr 33968201], length 123 12:50:04.892014 IP 172.16.31.52.34514 > 172.16.31.50.80: Flags [.], ack 124, win 457, options [nop,nop,TS val 33968205 ecr 47862911], length 0
6.查看apache的访问日志
[root@proxy ~]# tail /var/log/httpd/access_log 172.16.31.188 - - [14/Jan/2015:12:48:53 +0800] "GET /bg-upper.png HTTP/1.1" 304 - "http://www1.stu31.com/" "Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36" 172.16.31.188 - - [14/Jan/2015:12:49:05 +0800] "GET / HTTP/1.1" 200 11197 "-" "Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36" 172.16.31.188 - - [14/Jan/2015:12:49:05 +0800] "GET /tomcat.css HTTP/1.1" 304 - "http://www1.stu31.com/" "Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36" 172.16.31.188 - - [14/Jan/2015:12:49:05 +0800] "GET /tomcat.png HTTP/1.1" 304 - "http://www1.stu31.com/" "Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36" 172.16.31.188 - - [14/Jan/2015:12:49:59 +0800] "GET / HTTP/1.1" 200 11197 "-" "Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36" 172.16.31.188 - - [14/Jan/2015:12:49:59 +0800] "GET /tomcat.png HTTP/1.1" 304 - "http://www1.stu31.com/" "Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36" 172.16.31.188 - - [14/Jan/2015:12:49:59 +0800] "GET /tomcat.css HTTP/1.1" 304 - "http://www1.stu31.com/" "Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36" 172.16.31.188 - - [14/Jan/2015:12:50:05 +0800] "GET / HTTP/1.1" 200 11197 "-" "Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36" 172.16.31.188 - - [14/Jan/2015:12:50:06 +0800] "GET /tomcat.css HTTP/1.1" 304 - "http://www1.stu31.com/" "Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36" 172.16.31.188 - - [14/Jan/2015:12:50:06 +0800] "GET /tomcat.png HTTP/1.1" 304 - "http://www1.stu31.com/" "Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36"
二.配置apache通过proxy_ajp模块与Tomcat连接
1.配置ajp的配置文件
创建配置文件: [root@proxy conf.d]# cp mod_proxy_http.conf mod_proxy_ajp.conf [root@proxy conf.d]# ls mod_dnssd.conf mod_proxy_ajp.conf mod_proxy_http.conf README welcome.conf #需要将前面的http连接器的配置文件更改名称,不然httpd服务器加载。 [root@proxy conf.d]# mv mod_proxy_http.conf mod_proxy_http.conf.bak [root@proxy conf.d]# vim mod_proxy_ajp.conf NameVirtualHost *:80 <VirtualHost *:80> ServerName www1.stu31.com ProxyVia On ProxyRequests Off ProxyPreserveHost On <proxy *> Order deny,allow Allow from all </proxy> ProxyPass / ajp://172.16.31.50:8009/ ProxyPassReverse / ajp://172.16.31.50:8009/ <location /> Order deny,allow Allow from all </location> </VirtualHost>
2.关于如上apache指令的说明:
ProxyPreserveHost {On|Off}:如果启用此功能,代理会将用户请求报文中的Host:行发送给后端的服务器,而不再使用ProxyPass指定的服务器地址。如果想在反向代理中支持虚拟主机,则需要开启此项,否则就无需打开此功能。
ProxyVia {On|Off|Full|Block}:用于控制在http首部是否使用Via:,主要用于在多级代理中控制代理请求的流向。默认为Off,即不启用此功能;On表示每个请求和响应报文均添加Via:;Full表示每个Via:行都会添加当前apache服务器的版本号信息;Block表示每个代理请求报文中的Via:都会被移除。
ProxyRequests {On|Off}:是否开启apache正向代理的功能;启用此项时为了代理http协议必须启用mod_proxy_http模块。同时,如果为apache设置了ProxyPass,则必须将ProxyRequests设置为Off。
ProxyPass [path] !|url [key=value key=value ...]]:将后端服务器某URL与当前服务器的某虚拟路径关联起来作为提供服务的路径,path为当前服务器上的某虚拟路径,url为后端服务器上某URL路径。使用此指令时必须将ProxyRequests的值设置为Off。需要注意的是,如果path以“/”结尾,则对应的url也必须以“/”结尾,反之亦然。
另外,mod_proxy模块在httpd 2.1的版本之后支持与后端服务器的连接池功能,连接在按需创建在可以保存至连接池中以备进一步使用。连接池大小或其它设定可以通过在ProxyPass中使用key=value的方式定义。常用的key如下所示:
◇ min:连接池的最小容量,此值与实际连接个数无关,仅表示连接池最小要初始化的空间大小。
◇ max:连接池的最大容量,每个MPM都有自己独立的容量;都值与MPM本身有关,如Prefork的总是为1,而其它的则取决于ThreadsPerChild指令的值。
◇ loadfactor:用于负载均衡集群配置中,定义对应后端服务器的权重,取值范围为1-100。
◇ retry:当apache将请求发送至后端服务器得到错误响应时等待多长时间以后再重试。单位是秒钟。
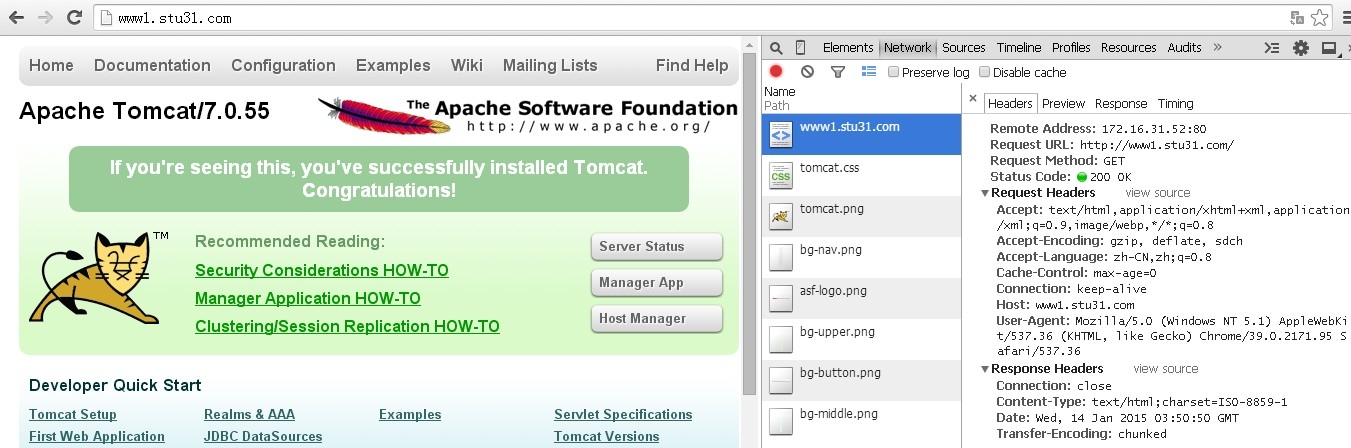
3.重启httpd服务器访问测试
#service httpd restart
4.在访问时抓取后端tomcat服务器8009端口的数据报文
[root@tom1 tomcat]# tcpdump -nn -i eth0 port 8009 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 11:59:09.124692 IP 172.16.31.52.37621 > 172.16.31.50.8009: Flags [P.], seq 652480048:652480426, ack 430562622, win 547, options [nop,nop,TS val 30912362 ecr 44296538], length 378 11:59:09.129104 IP 172.16.31.50.8009 > 172.16.31.52.37621: Flags [P.], seq 1:48, ack 378, win 277, options [nop,nop,TS val 44807150 ecr 30912362], length 47 11:59:09.129426 IP 172.16.31.50.8009 > 172.16.31.52.37621: Flags [.], seq 48:5840, ack 378, win 277, options [nop,nop,TS val 44807150 ecr 30912362], length 5792 11:59:09.129540 IP 172.16.31.52.37621 > 172.16.31.50.8009: Flags [.], ack 48, win 547, options [nop,nop,TS val 30912367 ecr 44807150], length 0 11:59:09.129655 IP 172.16.31.50.8009 > 172.16.31.52.37621: Flags [.], seq 5840:7288, ack 378, win 277, options [nop,nop,TS val 44807150 ecr 30912362], length 1448 11:59:09.129878 IP 172.16.31.52.37621 > 172.16.31.50.8009: Flags [.], ack 5840, win 638, options [nop,nop,TS val 30912367 ecr 44807150], length 0 11:59:09.129927 IP 172.16.31.50.8009 > 172.16.31.52.37621: Flags [P.], seq 7288:8240, ack 378, win 277, options [nop,nop,TS val 44807151 ecr 30912362], length 952 11:59:09.130021 IP 172.16.31.52.37621 > 172.16.31.50.8009: Flags [.], ack 7288, win 728, options [nop,nop,TS val 30912367 ecr 44807150], length 0 11:59:09.130510 IP 172.16.31.52.37621 > 172.16.31.50.8009: Flags [.], ack 8240, win 819, options [nop,nop,TS val 30912367 ecr 44807151], length 0 11:59:09.132924 IP 172.16.31.50.8009 > 172.16.31.52.37621: Flags [.], seq 8240:11136, ack 378, win 277, options [nop,nop,TS val 44807154 ecr 30912367], length 2896 11:59:09.133033 IP 172.16.31.50.8009 > 172.16.31.52.37621: Flags [P.], seq 11136:11261, ack 378, win 277, options [nop,nop,TS val 44807154 ecr 30912367], length 125 11:59:09.133248 IP 172.16.31.50.8009 > 172.16.31.52.37621: Flags [P.], seq 11261:11267, ack 378, win 277, options [nop,nop,TS val 44807154 ecr 30912367], length 6 11:59:09.133685 IP 172.16.31.52.37621 > 172.16.31.50.8009: Flags [.], ack 11261, win 909, options [nop,nop,TS val 30912371 ecr 44807154], length 0 11:59:09.133700 IP 172.16.31.52.37621 > 172.16.31.50.8009: Flags [.], ack 11267, win 909, options [nop,nop,TS val 30912371 ecr 44807154], length 0 11:59:09.250768 IP 172.16.31.52.37619 > 172.16.31.50.8009: Flags [P.], seq 388431840:388432292, ack 316918242, win 502, options [nop,nop,TS val 30912488 ecr 44296533], length 452 11:59:09.251575 IP 172.16.31.50.8009 > 172.16.31.52.37619: Flags [P.], seq 1:63, ack 452, win 277, options [nop,nop,TS val 44807272 ecr 30912488], length 62 11:59:09.251670 IP 172.16.31.50.8009 > 172.16.31.52.37619: Flags [P.], seq 63:69, ack 452, win 277, options [nop,nop,TS val 44807272 ecr 30912488], length 6 11:59:09.252330 IP 172.16.31.52.37619 > 172.16.31.50.8009: Flags [.], ack 63, win 502, options [nop,nop,TS val 30912490 ecr 44807272], length 0 11:59:09.252336 IP 172.16.31.52.37619 > 172.16.31.50.8009: Flags [.], ack 69, win 502, options [nop,nop,TS val 30912490 ecr 44807272], length 0 11:59:09.252608 IP 172.16.31.52.37617 > 172.16.31.50.8009: Flags [P.], seq 3441763038:3441763492, ack 2986701735, win 547, options [nop,nop,TS val 30912490 ecr 44296534], length 454 11:59:09.253725 IP 172.16.31.50.8009 > 172.16.31.52.37617: Flags [P.], seq 1:63, ack 454, win 277, options [nop,nop,TS val 44807274 ecr 30912490], length 62 11:59:09.253811 IP 172.16.31.50.8009 > 172.16.31.52.37617: Flags [P.], seq 63:69, ack 454, win 277, options [nop,nop,TS val 44807275 ecr 30912490], length 6 11:59:09.254596 IP 172.16.31.52.37617 > 172.16.31.50.8009: Flags [.], ack 63, win 547, options [nop,nop,TS val 30912492 ecr 44807274], length 0 11:59:09.254614 IP 172.16.31.52.37617 > 172.16.31.50.8009: Flags [.], ack 69, win 547, options [nop,nop,TS val 30912492 ecr 44807275], length 0
停止httpd服务器:
# service httpd stop
继续如下实验;
三.配置nginx反向代理访问tomcat
1.安装nginx
# yum install nginx-1.6.2-1.el6.ngx.x86_64.rpm
2.配置nginx的配置文件
配置nginx服务器将动态内容反向代理到后端tomcat服务器,而静态内容直接访问本地的nginx服务器
[root@proxy nginx]# pwd
/etc/nginx
[root@proxy nginx]# vim conf.d/default.conf
server {
listen 80;
server_name localhost;
#charset koi8-r;
#access_log /var/log/nginx/log/host.access.log main;
location / {
root /usr/share/nginx/html;
index index.html index.htm;
}
location ~* \.(jsp|do)$ {
proxy_pass http://172.16.31.50:80;
}
}3.启动nginx服务访问测试
#service nginx start
动态内容就转发到后端tomcat服务器了:
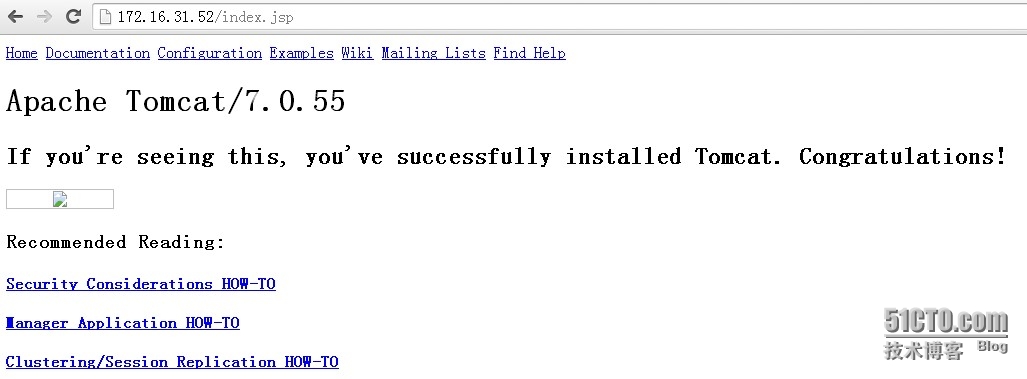
静态内容就在本地nginx服务器进行:
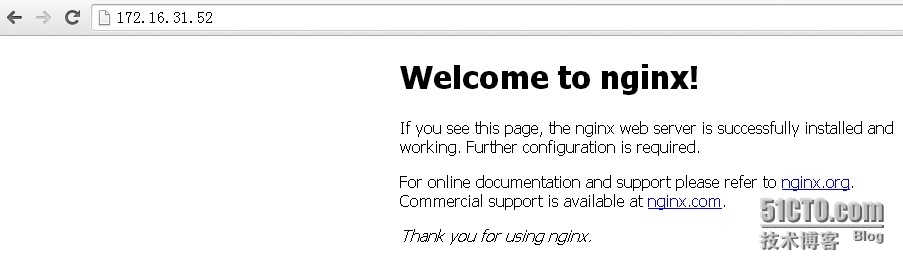 基于nginx反向代理就实现了,关闭nginx服务器:
基于nginx反向代理就实现了,关闭nginx服务器:
#service nginx stop
继续如下实验
四.配置apache通过mod_jk模块与Tomcat连接
mod_jk是ASF的一个项目,是一个工作于apache端基于AJP协议与Tomcat通信的连接器,它是apache的一个模块,是AJP协议的客户端(服务端是Tomcat的AJP连接器)。
1.开发环境部署
# yum groupinstall Development Tools # yum install -y httpd-devel
2.安装第三方的mod_jk模块
[root@proxy ~]# tar xf tomcat-connectors-1.2.40-src.tar.gz [root@proxy ~]# cd tomcat-connectors-1.2.40-src [root@proxy tomcat-connectors-1.2.40-src]# cd native/ [root@proxy native]# ./configure --with-apxs=`which apxs` [root@proxy native]# make && make install
3.查看安装的mod_jk模块
# ls /usr/lib64/httpd/modules/ | grep mod_jk
mod_jk.so
4.装载mod_jk模块到httpd服务器
将原有的httpd的配置文件直接备份,不然启动httpd服务时会加载其他配置文件哦!
apache要使用mod_jk连接器,需要在启动时加载此连接器模块。为了便于管理与mod_jk模块相关的配置,这里使用一个专门的配置文件/etc/httpd/conf.d/mod_jk.conf来保存相关指令及其设置。其内容如下:
#vim /etc/httpd/conf.d/mod_jk.conf LoadModule jk_module modules/mod_jk.so JkWorkersFile /etc/httpd/conf.d/workers.properties JkLogFile logs/mod_jk.log JkLogLevel debug JkMount /status ! JkMount /* TomcatA
除了需要使用LoadModule指令在apache中装载模块外,mod_jk还需要在apache的主配置文件中设置其它一些指令来配置其工作属性。如JkWorkersFile则用于指定保存了worker相关工作属性定义的配置文件,JkLogFile则用于指定mod_jk模块的日志文件,JkLogLevel则可用于指定日志的级别(info, error, debug),此外还可以使用JkRequestLogFormat自定义日志信息格式。而JkMount(格式: JkMount <URL to match> <Tomcat worker name>)指定则用于控制URL与Tomcat workers的对应关系。
对于apache代理来说,每一个后端的Tomcat实例中的engine都可以视作一个worker,而每一个worker的地址、连接器的端口等信息都需要在apache端指定以便apache可以识别并使用这些worker。约定俗成,配置这些信息的文件通常为workers.properties,其具体路径则是使用前面介绍过的JkWorkersFile指定的,在apache启动时,mod_jk会扫描此文件获取每一个worker的配置信息。比如,我们这里使用/etc/httpd/conf/workers.properties。
workers.properties文件一般由两类指令组成:一是mod_jk可以连接的各worker名称列表,二是每一个worker的属性配置信息。它们分别遵循如下使用语法。
worker.list = < a comma separated list of worker names > worker. <worker name> .<property> = <property value>
其中worker.list指令可以重复指定多次,而worker name则是Tomcat中engine组件jvmRoute参数的值。如:
worker.TomcatA.host=172.16.31.50
根据其工作机制的不同,worker有多种不同的类型,这是需要为每个worker定义的一项属性woker.<work name>.type。常见的类型如下:
◇ ajp13:此类型表示当前worker为一个运行着的Tomcat实例。
◇ lb:lb即load balancing,专用于负载均衡场景中的woker;此worker并不真正负责处理用户请求,而是将用户请求调度给其它类型为ajp13的worker。
◇ status:用户显示分布式环境中各实际worker工作状态的特殊worker,它不处理任何请求,也不关联到任何实际工作的worker实例。具体示例如请参见后文中的配置。
worker其它常见的属性说明:
◇ host:Tomcat 7的worker实例所在的主机;
◇ port:Tomcat 7实例上AJP1.3连接器的端口;
◇ connection_pool_minsize:最少要保存在连接池中的连接的个数;默认为pool_size/2;
◇ connection_pool_timeout:连接池中连接的超时时长;
◇ mount:由当前worker提供的context路径,如果有多个则使用空格格开;此属性可以由JkMount指令替代;
◇ retries:错误发生时的重试次数;
◇ socket_timeout:mod_jk等待worker响应的时长,默认为0,即无限等待;
◇ socket_keepalive:是否启用keep alive的功能,1表示启用,0表示禁用;
◇ lbfactor:worker的权重,可以在负载均衡的应用场景中为worker定义此属性;
另外,在负载均衡模式中,专用的属性还有:
◇balance_workers:用于负载均衡模式中的各worker的名称列表,需要注意的是,出现在此处的worker名称一定不能在任何worker.list属性列表中定义过,并且worker.list属性中定义的worker名字必须包含负载均衡worker。具体示例请参见后文中的定义。
◇ method:可以设定为R、T或B;默认为R,即根据请求的个数进行调度;T表示根据已经发送给worker的实际流量大小进行调度;B表示根据实际负载情况进行调度。
◇sticky_session:在将某请求调度至某worker后,源于此址的所有后续请求都将直接调度至此worker,实现将用户session与某worker绑定。默认为值为1,即启用此功能。如果后端的各worker之间支持session复制,则可以将此属性值设为0.
根据前文中的指定,这里使用/etc/httpd/conf.d/workers.properties来定义一个名为TomcatA的worker,并为其指定几个属性。文件内容如下:
#vim /etc/httpd/conf.d/workers.properties worker.list=TomcatA,StatA worker.TomcatA.port=8009 worker.TomcatA.host=172.16.31.50 worker.TomcatA.type=ajp13
至此,一个基于mod_jk模块与后端名为TomcatA的worker通信的配置已经完成,重启httpd服务即可生效。
5.重启httpd服务访问测试。
#service httpd start
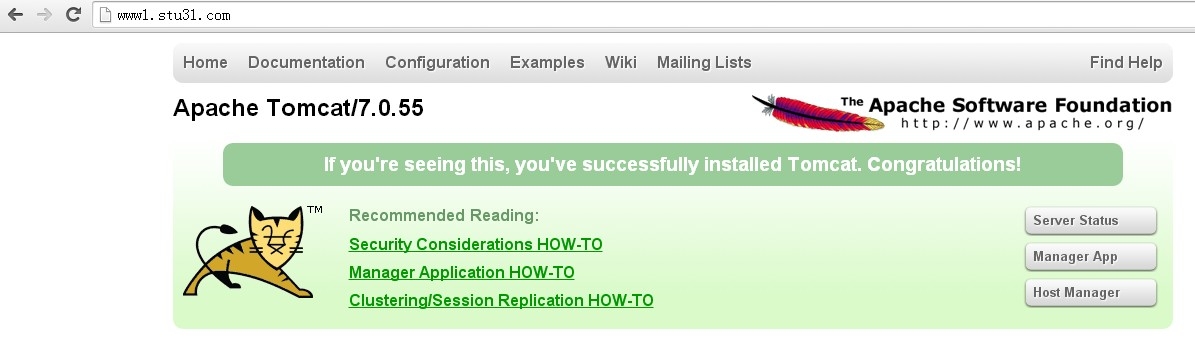
6.同样捕获访问后端tomcat的报文
[root@tom1 tomcat]# tcpdump -nn -i eth0 port 8009 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 12:01:03.985051 IP 172.16.31.52.37622 > 172.16.31.50.8009: Flags [S], seq 4216573225, win 14600, options [mss 1460,sackOK,TS val 31027224 ecr 0,nop,wscale 5], length 0 12:01:03.985084 IP 172.16.31.50.8009 > 172.16.31.52.37622: Flags [S.], seq 2858416450, ack 4216573226, win 14480, options [mss 1460,sackOK,TS val 44922006 ecr 31027224,nop,wscale 6], length 0 12:01:03.985769 IP 172.16.31.52.37622 > 172.16.31.50.8009: Flags [.], ack 1, win 457, options [nop,nop,TS val 31027226 ecr 44922006], length 0 12:01:03.987013 IP 172.16.31.52.37622 > 172.16.31.50.8009: Flags [P.], seq 1:443, ack 1, win 457, options [nop,nop,TS val 31027226 ecr 44922006], length 442 12:01:03.987144 IP 172.16.31.50.8009 > 172.16.31.52.37622: Flags [.], ack 443, win 243, options [nop,nop,TS val 44922008 ecr 31027226], length 0 12:01:03.989937 IP 172.16.31.50.8009 > 172.16.31.52.37622: Flags [P.], seq 1:48, ack 443, win 243, options [nop,nop,TS val 44922011 ecr 31027226], length 47 12:01:03.990032 IP 172.16.31.50.8009 > 172.16.31.52.37622: Flags [.], seq 48:2944, ack 443, win 243, options [nop,nop,TS val 44922011 ecr 31027226], length 2896 12:01:03.990069 IP 172.16.31.50.8009 > 172.16.31.52.37622: Flags [.], seq 2944:5840, ack 443, win 243, options [nop,nop,TS val 44922011 ecr 31027226], length 2896 12:01:03.990100 IP 172.16.31.50.8009 > 172.16.31.52.37622: Flags [.], seq 5840:7288, ack 443, win 243, options [nop,nop,TS val 44922011 ecr 31027226], length 1448 12:01:03.990110 IP 172.16.31.50.8009 > 172.16.31.52.37622: Flags [P.], seq 7288:8240, ack 443, win 243, options [nop,nop,TS val 44922011 ecr 31027226], length 952 12:01:03.990225 IP 172.16.31.50.8009 > 172.16.31.52.37622: Flags [.], seq 8240:11136, ack 443, win 243, options [nop,nop,TS val 44922011 ecr 31027226], length 2896 12:01:03.990258 IP 172.16.31.50.8009 > 172.16.31.52.37622: Flags [P.], seq 11136:11261, ack 443, win 243, options [nop,nop,TS val 44922011 ecr 31027226], length 125 12:01:03.991990 IP 172.16.31.52.37622 > 172.16.31.50.8009: Flags [.], ack 48, win 457, options [nop,nop,TS val 31027232 ecr 44922011], length 0 12:01:03.992006 IP 172.16.31.52.37622 > 172.16.31.50.8009: Flags [.], ack 8240, win 547, options [nop,nop,TS val 31027232 ecr 44922011], length 0 12:01:03.992008 IP 172.16.31.52.37622 > 172.16.31.50.8009: Flags [.], ack 11261, win 638, options [nop,nop,TS val 31027232 ecr 44922011], length 0 12:01:03.992147 IP 172.16.31.50.8009 > 172.16.31.52.37622: Flags [P.], seq 11261:11267, ack 443, win 243, options [nop,nop,TS val 44922013 ecr 31027232], length 6 12:01:03.992508 IP 172.16.31.52.37622 > 172.16.31.50.8009: Flags [.], ack 11267, win 638, options [nop,nop,TS val 31027233 ecr 44922013], length 0 12:01:04.091546 IP 172.16.31.52.37623 > 172.16.31.50.8009: Flags [S], seq 3829641182, win 14600, options [mss 1460,sackOK,TS val 31027331 ecr 0,nop,wscale 5], length 0 12:01:04.091571 IP 172.16.31.50.8009 > 172.16.31.52.37623: Flags [S.], seq 4142766846, ack 3829641183, win 14480, options [mss 1460,sackOK,TS val 44922112 ecr 31027331,nop,wscale 6], length 0 12:01:04.091590 IP 172.16.31.52.37624 > 172.16.31.50.8009: Flags [S], seq 2391558172, win 14600, options [mss 1460,sackOK,TS val 31027331 ecr 0,nop,wscale 5], length 0 12:01:04.091594 IP 172.16.31.50.8009 > 172.16.31.52.37624: Flags [S.], seq 1706724513, ack 2391558173, win 14480, options [mss 1460,sackOK,TS val 44922112 ecr 31027331,nop,wscale 6], length 0 12:01:04.093174 IP 172.16.31.52.37623 > 172.16.31.50.8009: Flags [.], ack 1, win 457, options [nop,nop,TS val 31027332 ecr 44922112], length 0 12:01:04.093210 IP 172.16.31.52.37624 > 172.16.31.50.8009: Flags [.], ack 1, win 457, options [nop,nop,TS val 31027332 ecr 44922112], length 0 12:01:04.093217 IP 172.16.31.52.37624 > 172.16.31.50.8009: Flags [P.], seq 1:519, ack 1, win 457, options [nop,nop,TS val 31027332 ecr 44922112], length 518 12:01:04.093227 IP 172.16.31.50.8009 > 172.16.31.52.37624: Flags [.], ack 519, win 243, options [nop,nop,TS val 44922114 ecr 31027332], length 0 12:01:04.093251 IP 172.16.31.52.37623 > 172.16.31.50.8009: Flags [P.], seq 1:517, ack 1, win 457, options [nop,nop,TS val 31027334 ecr 44922112], length 516 12:01:04.093256 IP 172.16.31.50.8009 > 172.16.31.52.37623: Flags [.], ack 517, win 243, options [nop,nop,TS val 44922114 ecr 31027334], length 0 12:01:04.094620 IP 172.16.31.50.8009 > 172.16.31.52.37623: Flags [P.], seq 1:63, ack 517, win 243, options [nop,nop,TS val 44922115 ecr 31027334], length 62 12:01:04.094811 IP 172.16.31.50.8009 > 172.16.31.52.37623: Flags [P.], seq 63:69, ack 517, win 243, options [nop,nop,TS val 44922116 ecr 31027334], length 6 12:01:04.095289 IP 172.16.31.52.37623 > 172.16.31.50.8009: Flags [.], ack 63, win 457, options [nop,nop,TS val 31027336 ecr 44922115], length 0 12:01:04.095300 IP 172.16.31.52.37623 > 172.16.31.50.8009: Flags [.], ack 69, win 457, options [nop,nop,TS val 31027336 ecr 44922116], length 0 12:01:04.096211 IP 172.16.31.50.8009 > 172.16.31.52.37624: Flags [P.], seq 1:63, ack 519, win 243, options [nop,nop,TS val 44922117 ecr 31027332], length 62 12:01:04.097810 IP 172.16.31.52.37624 > 172.16.31.50.8009: Flags [.], ack 63, win 457, options [nop,nop,TS val 31027338 ecr 44922117], length 0 12:01:04.097928 IP 172.16.31.50.8009 > 172.16.31.52.37624: Flags [P.], seq 63:69, ack 519, win 243, options [nop,nop,TS val 44922119 ecr 31027338], length 6 12:01:04.099234 IP 172.16.31.52.37624 > 172.16.31.50.8009: Flags [.], ack 69, win 457, options [nop,nop,TS val 31027340 ecr 44922119], length 0
7.查看mod_jk的日志
[root@proxy conf.d]# cd /var/log/httpd/ [root@proxy httpd]# ls access_log jk-runtime-status.1114 mod_jk.log error_log jk-runtime-status.1114.lock
[root@proxy httpd]# tail mod_jk.log [Wed Jan 14 12:41:50.646 2015] [1123:140644506580960] [debug] ajp_unmarshal_response::jk_ajp_common.c (705): status = 304 [Wed Jan 14 12:41:50.646 2015] [1123:140644506580960] [debug] ajp_unmarshal_response::jk_ajp_common.c (712): Number of headers is = 2 [Wed Jan 14 12:41:50.646 2015] [1123:140644506580960] [debug] ajp_unmarshal_response::jk_ajp_common.c (768): Header[0] [ETag] = [W/"5103-1405694376000"] [Wed Jan 14 12:41:50.646 2015] [1123:140644506580960] [debug] ajp_unmarshal_response::jk_ajp_common.c (768): Header[1] [Content-Length] = [0] [Wed Jan 14 12:41:50.646 2015] [1123:140644506580960] [debug] ajp_connection_tcp_get_message::jk_ajp_common.c (1403): received from ajp13 pos=0 len=2 max=8192 [Wed Jan 14 12:41:50.646 2015] [1123:140644506580960] [debug] ajp_connection_tcp_get_message::jk_ajp_common.c (1403): 0000 05 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 - ................ [Wed Jan 14 12:41:50.646 2015] [1123:140644506580960] [debug] ajp_process_callback::jk_ajp_common.c (2054): AJP13 protocol: Reuse is OK [Wed Jan 14 12:41:50.646 2015] [1123:140644506580960] [debug] ajp_reset_endpoint::jk_ajp_common.c (810): (TomcatA) resetting endpoint with socket 14 [Wed Jan 14 12:41:50.646 2015] [1123:140644506580960] [debug] ajp_done::jk_ajp_common.c (3144): recycling connection pool for worker TomcatA and socket 14 [Wed Jan 14 12:41:50.646 2015] [1123:140644506580960] [debug] jk_handler::mod_jk.c (2790): Service finished with status=304 for worker=TomcatA
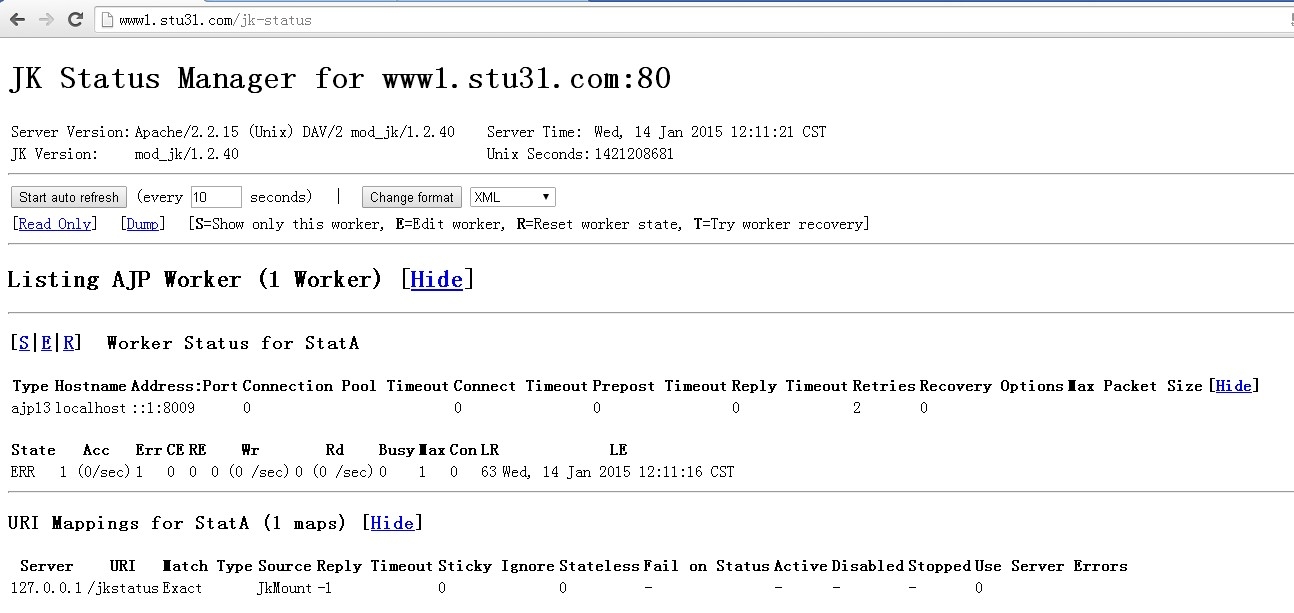
8.访问tomcat的状态页面
配置如下:
vim /etc/httpd/conf.d/mod_jk.conf LoadModule jk_module modules/mod_jk.so JkWorkersFile /etc/httpd/conf.d/workers.properties JkLogFile logs/mod_jk.log JkLogLevel debug JkMount /status ! JkMount /* TomcatA JkMount /jkstatus StatA
#vim /etc/httpd/conf.d/workers.properties worker.list=TomcatA,StatA worker.TomcatA.port=8009 worker.TomcatA.host=172.16.31.50 worker.TomcatA.type=ajp13 worker.TomcatA.type=status
重启httpd服务访问测试:
至此,各种tomcat的连接器的介绍就完成了!
本文出自 “飞雪连天射白鹿” 博客,请务必保留此出处http://sohudrgon.blog.51cto.com/3088108/1605008
Tomcat基础配置(2)-Tomcat连接器
