首页 > 代码库 > https
https
########https#######
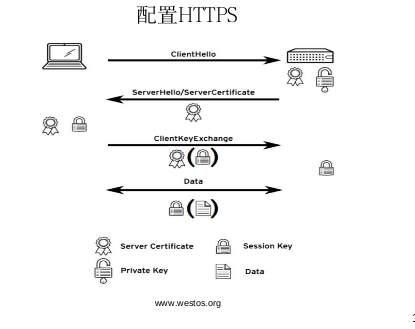
1.https定义
Hyper text transfer protocol over Secure socker layer
通过ssl
如果加密的通信非常重要,而经过验证的身份不重要,管理员可以通过生成self-
signed certificate来避免与认证机构进行交互所带来的复杂性。
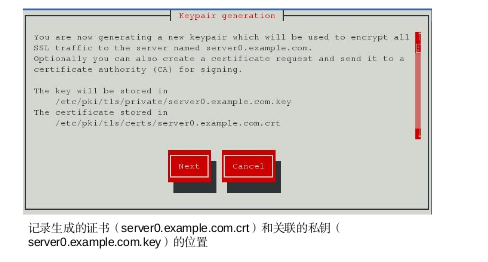
使用genkey实用程序(通过crypto-utils软件包分发),生成自签名证书及其关联的
私钥。为了简化起见,genkey将在“正确”的位置(/etc/pki/tls目录)创建证书及其
关联的密钥。相应地,必须以授权用户(root)身份运行该实用程序。
2.配置
yum install mod_ssl -y
yum install crypto-utils -y
genkey www.westos.com
[root@localhost virtual]# genkey www.westos.com ##配置钥匙

@@@@@@@
/usr/bin/keyutil -c makecert -g 1024 -s "CN=www.westos.com, OU=linux, O=westos, L=xi‘an, ST=shannxi, C=CN" -v 1 -a -z /etc/pki/tls/.rand.6165 -o /etc/pki/tls/certs/www.westos.com.crt -k /etc/pki/tls/private/www.westos.com.key
cmdstr: makecert
cmd_CreateNewCert
command: makecert
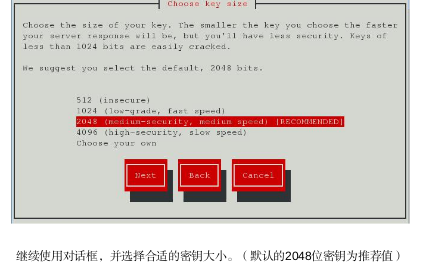
keysize = 1024 bits
subject = CN=www.westos.com, OU=linux, O=westos, L=xi‘an, ST=shannxi, C=CN
valid for 1 months
random seed from /etc/pki/tls/.rand.6165
output will be written to /etc/pki/tls/certs/www.westos.com.crt
output key written to /etc/pki/tls/private/www.westos.com.key
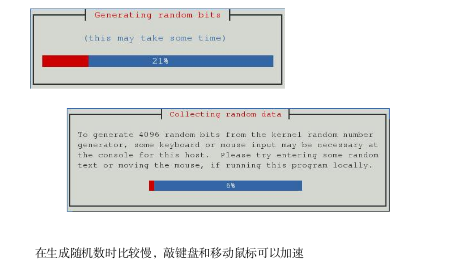
Generating key. This may take a few moments...
Made a key
Opened tmprequest for writing
/usr/bin/keyutil Copying the cert pointer
Created a certificate
Wrote 882 bytes of encoded data to /etc/pki/tls/private/www.westos.com.key
Wrote the key to:
/etc/pki/tls/private/www.westos.com.key
@@@@@@@@
/etc/pki/tls/private/www.westos.com.key
/etc/pki/tls/certs/www.westos.com.crt
vim /etc/httpd/conf.d/login.conf
[root@localhost conf.d]# ls
autoindex.conf login.conf php.conf squid.conf userdir.conf
default.conf news.conf README ssl.conf welcome.conf
[root@localhost conf.d]# vim ssl.conf ##添加加密字符文件
@@@@@@
# pass phrase. Note that a kill -HUP will prompt again. A new
# certificate can be generated using the genkey(1) command.
SSLCertificateFile /etc/pki/tls/certs/www.westos.com.crt
# Server Private Key:
# If the key is not combined with the certificate, use this
# directive to point at the key file. Keep in mind that if
# you‘ve both a RSA and a DSA private key you can configure
# both in parallel (to also allow the use of DSA ciphers, etc.)
SSLCertificateKeyFile /etc/pki/tls/private/www.westos.com.key
# Server Certificate Chain:
# Point SSLCertificateChainFile at a file containing the
# concatenation of PEM encoded CA certificates which form the
# certificate chain for the server certificate. Alternatively
@@@@@@@
[root@localhost conf.d]# vim login.conf
<Virtualhost *:443>
ServerName "login.westos.com"
DocumentRoot "/var/www/virtual/login.westos.com/html"
CustomLog "logs/login.log" combined
SSLEngine on ##开启https功能
SSLCertificateFile /etc/pki/tls/certs/www.westos.com.crt ##证书
SSLCertificateKeyFile /etc/pki/tls/private/www.westos.com.key ##密钥
</Virtualhost>
<Directory "/var/www/virtual/login.westos.com/html">
Require all granted
</Directory>
</Virtualhost *:80> ##网页重写实现自动访问(把所有80端口的请求全部重定向由https来处理)
ServerName login.westos.com
RewriteEngine on
RewriteRule ^(/.*)$ https://%{HTTP_HOST}$1 [redirect=301]
</Virtualhost>
^(/.*)$ http://%{HTTP_HOST}$1 [redirect=301]
^(/.*)$ ##客户主机在地址栏中写入的所有字符,除过换行符
http:// ##定向成为的访问协议
%{HTTP_HOST} ##客户请求主机
$1##$1的值就表示^(/.*)$ 的值
[redirect=301] ##临时重定向 302表示永久定向
mkdir /var/www/virtual/login.westos.com/html -p
vim /var/www/virtual/login.westos.com/html/index.html
systemctl restart httpd
测试:
在客户主机中添加解析
172.25.254.113 login.westos.com
访问http://login.westos.com 会实现自动调转
https://login.westos.com 实现网页数据加密传送
本文出自 “AELY木” 博客,请务必保留此出处http://12768057.blog.51cto.com/12758057/1926547
https
