首页 > 代码库 > OSSEC 加固linux系统详细配置
OSSEC 加固linux系统详细配置
ossec官方网站http://www.ossec.net/
ossec帮助文档http://ossec-docs.readthedocs.org/en/latest/manual/index.html
OSSEC是一个开源的基于主机的入侵检测系统,执行日志分析,文件完整性检查,政策监控,rootkit检测,实时报警和积极响应。
它可以运行在大多数的操作系统,包括Linux,MacOS的时,Solaris,HP-UX,AIX和Windows
最新稳定版为2.8 下载页面http://www.ossec.net/?page_id=19
Ossec部署方式为C/S,以下server:192.168.22.240 client:192.168.22.241
先关闭selinux,安装常用包
环境 CentOS release 6.4(Final) x86_64
sed -i s/SELINUX=enforcing/SELINUX=disabled/g /etc/sysconfig/selinux yum install gcc gcc-c++ vim wget lrzsz ntpdate sysstat dstat wget -y
安装服务端
Ip 192.168.22.240
yum install mysql mysql-server mysql-devel httpd php php-mysql –y tar -xzf ossec-hids-2.8.tar.gz cd ossec-hids-2.8 cd src/ # make setdb Error: PostgreSQL client libraries notinstalled. Info: Compiled with MySQL support. #ossec支持mysql数据库 # ./install
下面是安装过程
en #选择语言 Enter #继续 Server #安装为server /usr/local/ossec #安装目录 3.1- Do you want e-mail notification? (y/n)[y]: y -What‘s your e-mail address? Your_mail@163.com -What‘s your SMTP server ip/host? 127.0.0.1 Enter # Running syscheck (integrity check daemon) Enter # Running rootcheck (rootkit detection) Enter #Active response enabled Enter # firewall-drop enabled (local) for levels >= 6 Do you want to add more IPs to the whitelist? (y/n)? [n]: y #设置ip白名单 -IPs (space separated): 3.5- Do you want to enable remote syslog(port 514 udp)? (y/n) [y]:Enter Enter #开始安装
安装完成的配置文件及选项:
/usr/local/ossec/bin/ossec-control start /usr/local/ossec/bin/ossec-control stop /usr/local/ossec/etc/ossec.conf /usr/local/ossec/bin/manage_agents
# /usr/local/ossec/bin/ossec-control --help
Usage: /usr/local/ossec/bin/ossec-control{start|stop|restart|status|enable|disable}# /usr/local/ossec/bin/ossec-control enable--help Invalid enable option. Enable options: database, client-syslog,agentless, debug Usage: /usr/local/ossec/bin/ossec-controlenable [database|client-syslog|agentless|debug]
/usr/local/ossec/bin/ossec-control enabledatabase # service mysqld start /usr/bin/mysql_secure_installation # mysql -uroot –p mysql> create database ossec; mysql> grantINSERT,SELECT,UPDATE,CREATE,DELETE,EXECUTE on ossec.* to ossec@localhostidentified by ‘ossec‘; mysql> grant INSERT,SELECT,UPDATE,CREATE,DELETE,EXECUTEon ossec.* to ossec@192.168.22.240 identified by‘ossec‘; #此句是为下面的analogi mysql> flush privileges; mysql> \q
[root@localhost ossec-hids-2.8]# mysql-uossec -p ossec < src/os_dbd/mysql.schema
Enter password:
vim /usr/local/ossec/etc/ossec.conf #在最后添加
<ossec_config> <database_output> <hostname>localhost</hostname> <username>ossec</username> <password>ossec</password> <database>ossec</database> <type>mysql</type> </database_output> </ossec_config>
添加128行内容,允许此网段的日志
<remote> 127 <connection>syslog</connection> 128<allowed-ips>192.168.22.0/24</allowed-ips> 129 </remote>
/usr/local/ossec/bin/ossec-control restart
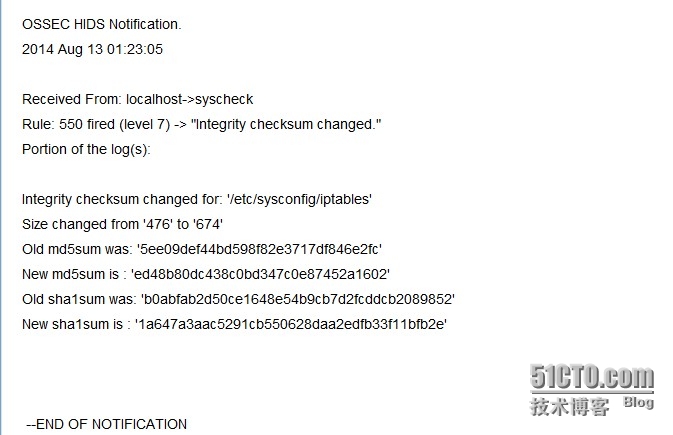
此时,邮箱已经收到邮件了
下面添加agent客户端
# /usr/local/ossec/bin/manage_agents (A)dd an agent (A). (E)xtract key for an agent (E). (L)ist already added agents (L). (R)emove an agent (R). (Q)uit. #下面依次: A #add Please provide the following: *A name for the new agent: agent1 *The IP Address of the new agent: 192.168.22.241 *An ID for the new agent[001]: 001 Agent information: ID:001 Name:agent1 IPAddress:192.168.22.241 Confirm adding it?(y/n): y Agent added. **************************************** * OSSEC HIDS v2.8 Agent manager. * * The following options are available: * **************************************** (A)dd an agent (A). (E)xtract key for an agent (E). (L)ist already added agents (L). (R)emove an agent (R). (Q)uit. Choose your action: A,E,L,R or Q: E Available agents: ID: 001, Name: agent1, IP: 192.168.22.241 Provide the ID of the agent to extract thekey (or ‘\q‘ to quit): 001 Agent key information for ‘001‘ is: MDAxIGFnZW50MSAxOTIuMTY4LjIyLjI0MSBmYTcxYWE1ZWQxYTg0YTM3MDcwNTFkMGRkMDY4NTcyNDQ5NDY2MWRkYTI3ZTMxZsNhZDd3YmFjZjddZTFkMmNj ** Press ENTER to return to the main menu. Choose your action: A,E,L,R or Q: Q
# netstat -unlp|grep ossec #ossec通信是用udp 514,1514端口,
udp 0 0 0.0.0.0:514 0.0.0.0:* 4511/ossec-remoted udp 0 0 0.0.0.0:1514 0.0.0.0:* 4513/ossec-remoted
vim /etc/sysconfig/iptables #开启iptables的端口 -A INPUT -m state --state NEW -m udp -p udp--dport 514 -j ACCEPT -A INPUT -m state --state NEW -m udp -p udp--dport 1514 -j ACCEPT service iptables restart
安装客户端
Ip 192.168.22.241
tar -xzf ossec-hids-2.8.tar.gz # cd ossec-hids-2.8 # ./install.sh Y #默认为en Enter #开始安装 Agent #作为代理 /usr/local/ossec #安装目录 192.168.22.240 #添加server的ip Enter #Running syscheck (integrity check daemon) Enter #Running rootcheck (rootkit detection) Enter #active response Enter #开始安装
安装后的配置
/usr/local/ossec/bin/ossec-control start /usr/local/ossec/bin/ossec-control stop /usr/local/ossec/etc/ossec.conf /usr/local/ossec/bin/manage_agents
设置agent
# /usr/local/ossec/bin/manage_agents **************************************** * OSSEC HIDS v2.8 Agent manager. * * The following options are available: * **************************************** (I)mport key from the server (I). (Q)uit. Choose your action: I or Q: I * Provide the Key generated by the server. * The best approach is to cut and paste it. *** OBS: Do not include spaces or newlines. Paste it here (or ‘\q‘ to quit): MDAxIGFnZW50MSAxOTIuMTY4LjIyLjI0zSBmYTcxYWE1ZWQxYTg0YTM3MDcwNTFkMGRkMDY4NTcyNDQ5NDY2MWRkYTI3ZTMxZTNdZDc3YmFjZjdmZTFk5mNj Agent information: ID:001 Name:agent1 IPAddress:192.168.22.241 Confirm adding it?(y/n): y Added. ** Press ENTER to return to the main menu. Choose your action: I or Q: Q
Ossec的日志
/usr/local/ossec/logs/ossec.log
安装web界面
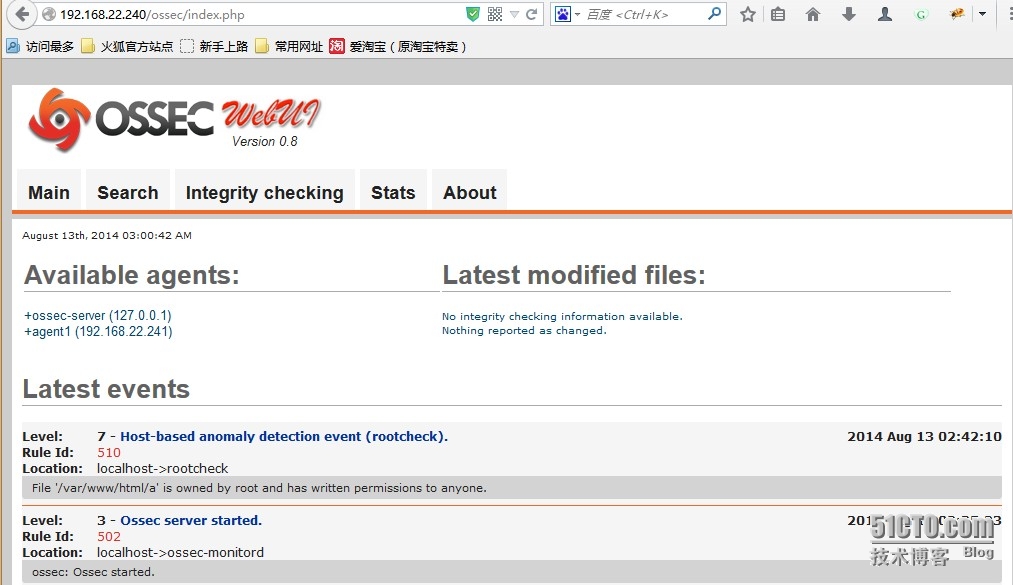
ossec-wui界面
cd /var/www unzip ossec-wui-master.zip mv ossec-wui-master html/ossec cd html/ossec/ # cat ossec_conf.php /* Ossec directory */ #$ossec_dir="/var/ossec"; $ossec_dir="/usr/local/ossec"; # ./setup.sh Setting up ossec ui... Username: ossec New password: Re-type new password: Adding password for user ossec Enter your web server user name (e.g.apache, www, nobody, www-data, ...) apache Enter your OSSEC install directory path(e.g. /var/ossec) /usr/local/ossec You must restart your web server after thissetup is done. Setup completed successfuly.
# vim /etc/httpd/conf.d/ossec.conf Alias /analogi /var/www/html/ossec <Directory /var/www/html/ossec> Order deny,allow Deny from all Allow from 192.168.22.0/24 Options -MultiViews AuthName "OSSEC AUTH" AuthType Basic AuthUserFile /var/www/html/ossec/.htpasswd Require valid-user </Directory>
别忘了把iptables的80打开
-A INPUT -m state --state NEW -m tcp -p tcp--dport 80 -j ACCEPT chown apache:apache * service httpd restart
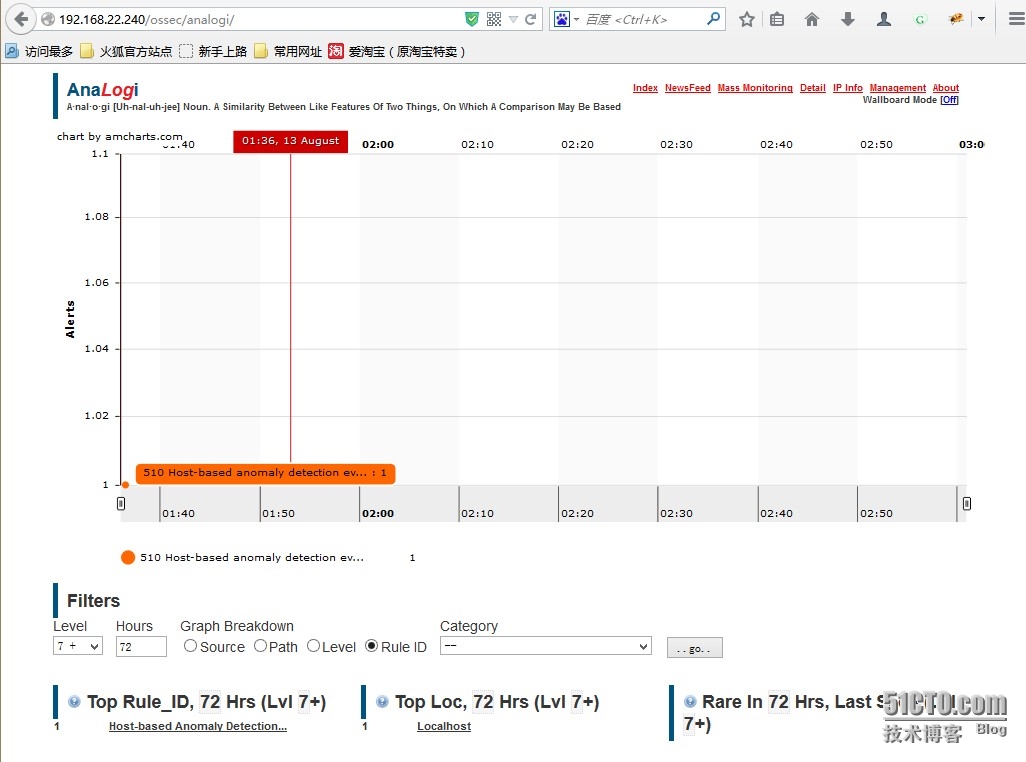
analogi界面
cd /var/www/html wgethttps://github.com/ECSC/analogi/archive/master.zip unzip analogi-master.zip mv analogi-master ossec/analogi chown apache.apache -R ossec cd ossec/analogi cp db_ossec.php.new db_ossec.php vim db_ossec.php define (‘DB_USER_O‘, ‘ossec‘); define (‘DB_PASSWORD_O‘, ‘ossec‘); define (‘DB_HOST_O‘, ‘localhost‘); define (‘DB_NAME_O‘, ‘ossec‘); vim /etc/httpd/conf.d/analogi.conf Alias /analogi /var/www/html/analogi <Directory /var/www/html/analogi> Order deny,allow Deny from all Allow from 192.168.22.0/24 </Directory>
查看状态信息
# /usr/local/ossec/bin/agent_control -lc OSSEC HIDS agent_control. List of availableagents: ID: 000, Name: localhost.localdomain (server), IP: 127.0.0.1,Active/Local ID: 001, Name: agent1, IP: 192.168.22.241, Active # /usr/local/ossec/bin/list_agents -a agent1-192.168.22.241 is available. # /usr/local/ossec/bin/ossec-control status ossec-monitord is running... ossec-logcollector is running... ossec-remoted is running... ossec-syscheckd is running... ossec-analysisd is running... ossec-maild is running... ossec-execd is running... ossec-dbd is running...
OSSEC的图形界面
analogi图形界面
收到ossec发送的邮件
本文出自 “一颗石头 BBOTTE的博客” 博客,请务必保留此出处http://bbotte.blog.51cto.com/6205307/1539285
