首页 > 代码库 > Cisco ASA站点间穿越nat互相访问的实验
Cisco ASA站点间穿越nat互相访问的实验
1、 实验拓扑图:
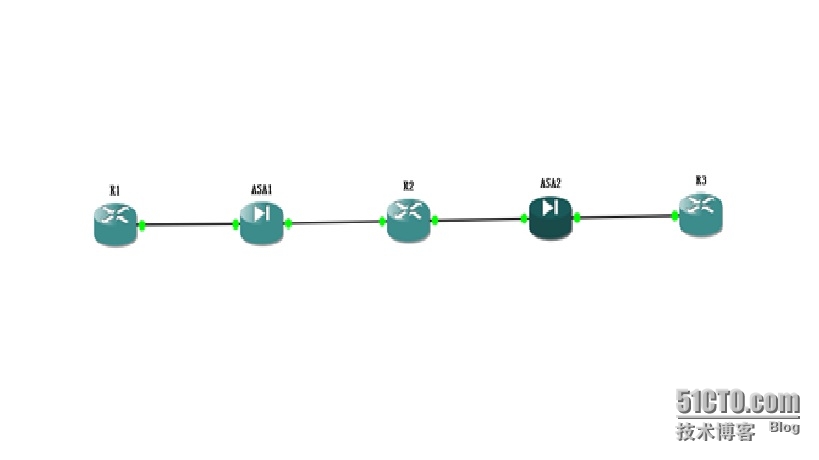
1、 实验说明:
R1作为A公司的站点1,内部有台1.1.1.1/32的服务器需要A公司站点2的管理员实行远程telnet的设备管理;
R5作为A公司的站点2,内部有台2.2.2.2/32的服务器需要A公司站点1的管理员实行远程telnet的设备管理;
设备之间都有ASA防火墙的安全保护,R2作为互联网的一台路由器;
2、 实验配置:
R1#show run
usernamecisco password 0 cisco
!
interfaceLoopback0 //站点2管理员通过该地址进行R1设备的管理
ip address 1.1.1.1 255.255.255.0
!
interfaceLoopback1 //正常通过NAT上网的用户地址段
ip address 10.10.10.10 255.255.255.0
!
interfaceFastEthernet0/0
ip address 172.16.255.1 255.255.255.192
duplex auto
speed auto
!
interfaceFastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
routerospf 1
log-adjacency-changes
network 1.1.1.0 0.0.0.255 area 1
network 10.10.10.0 0.0.0.255 area 1
network 172.16.255.0 0.0.0.63 area 1
!
ipforward-protocol nd
!
no iphttp server
no iphttp secure-server
!
control-plane
!
line con0
exec-timeout 0 0
logging synchronous
line aux0
line vty0 4
password cisco
login local
transport input telnet
ASA1#show run
interfaceEthernet0/0
nameif Inside
security-level 100
ip address 172.16.255.2 255.255.255.192
!
interfaceEthernet0/1
nameif Outside
security-level 0
ip address 202.16.1.2 255.255.255.248
!
access-listoutside extended permit ip 10.10.10.0 255.255.255.0 any
access-listout extended permit icmp any any
access-listout extended permit tcp host 202.16.1.12 host 202.16.1.5 eq telnet
nat-control
global(Outside) 1 interface
nat(Inside) 1 access-list outside
static(Inside,Outside) 202.16.1.5 1.1.1.1 netmask 255.255.255.255
access-groupout in interface Outside
!
routerospf 1
network 172.16.255.0 255.255.255.192 area 1
log-adj-changes
default-information originate always
!
routeOutside 0.0.0.0 0.0.0.0 202.16.1.1 1
R2#show run
interfaceFastEthernet0/0
ip address 202.16.1.1 255.255.255.248
duplex auto
speed auto
!
interfaceFastEthernet0/1
ip address 202.16.1.9 255.255.255.248
duplex auto
speed auto
ASA2#show run
interfaceEthernet0/0
nameif Inside
security-level 100
ip address 172.16.255.130 255.255.255.192
!
interfaceEthernet0/1
nameif Outside
security-level 0
ip address 202.16.1.10 255.255.255.248
!
access-listout extended permit icmp any any
access-listout extended permit tcp host 202.16.1.5 host 202.16.1.12 eq telnet
access-listinside_nat1_outside extended permit ip 10.10.20.0 255.255.255.0 any
global(Outside) 1 interface
nat(Inside) 1 access-list inside_nat1_outside
static(Inside,Outside) 202.16.1.12 2.2.2.2 netmask 255.255.255.255
access-groupout in interface Outside
!
routerospf 10
network 172.16.255.128 255.255.255.192 area 0
log-adj-changes
default-information originate always
!
routeOutside 0.0.0.0 0.0.0.0 202.16.1.9 1
R3#show run
usernamecisco password 0 cisco
!
interfaceLoopback0 //站点2路由器需要通过该地址被管理
ip address 2.2.2.2 255.255.255.0
!
interfaceLoopback1 //用户上网地址
ip address 10.10.20.10 255.255.255.0
!
interfaceFastEthernet0/0
ip address 172.16.255.129 255.255.255.192
duplex auto
speed auto
!
routerospf 10
log-adjacency-changes
network 2.2.2.0 0.0.0.255 area 0
network 10.10.20.0 0.0.0.255 area 0
network 172.16.255.128 0.0.0.63 area 0
!
line vty0 4
password cisco
login local
transport input telnet
3、 站点间的互访测试:
R1#ping 202.16.1.9 source 10.10.10.10 //用户访问互联网
Typeescape sequence to abort.
Sending5, 100-byte ICMP Echos to 202.16.1.9, timeout is 2 seconds:
Packetsent with a source address of 10.10.10.10
!!!!!
Successrate is 100 percent (5/5), round-trip min/avg/max = 16/27/40 ms
Ciscoasa1# show xlate
2 in use,3 most used
PAT Global 202.16.1.2(2) Local10.10.10.10 ICMP id 23 //执行了正常的PAT转换
R1#telnet 202.16.1.12 /source-interfaceloopback 0 //正常的管理站点2设备
Trying 202.16.1.12 ... Open
!
User Access Verification
!
Username: cisco
Password:
R3>en
Password:
Password:
R3#
Ciscoasa1#show xlate //原因在于防火墙中有这条静态映射条目
1 in use, 3 most used
Global 202.16.1.5 Local 1.1.1.1
反之从R3– R1的测试结果是一样的,就由各位IT自己测试了。
本文出自 “我的技术博客” 博客,谢绝转载!
Cisco ASA站点间穿越nat互相访问的实验
