首页 > 代码库 > ssh使用密钥验证
ssh使用密钥验证
如果使用密码验证的方式连接服务器,虽说ssh所有传输的数据都会被加密,但有可能被有心人抓包下来破解或者服务器被冒充的风险。使用密钥验证的话可以有效解决这些安全隐患,就是你必须为自己创建一对密匙,并把公用密匙放在需要访问的服务器上。如果你要连接到SSH服务器上,客户端软件就会向服务器发出请求,请求用你的密匙进行安全验证。服务器收到请求之后,先在该服务器上你的主目录下寻找你的公用密匙,然后把它和你发送过来的公用密匙进行比较。如果两个密匙一致,服务器就用公用密匙加密“质询”(challenge)并把它发送给客户端软件。客户端软件收到“质询”之后就可以用你的私人密匙解密再把它发送给服务器
window下使用xshell生成密钥与linux的ssh进行连接
1.新建连接
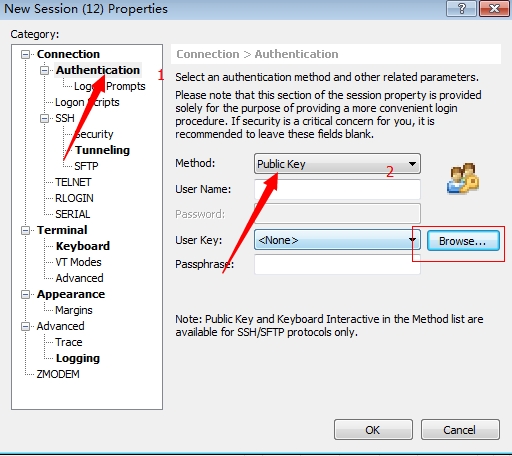
2.创建密钥
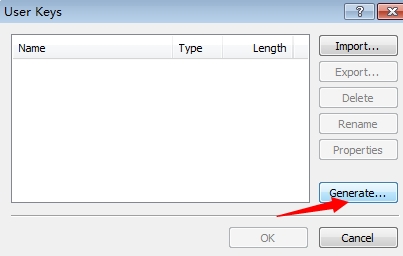
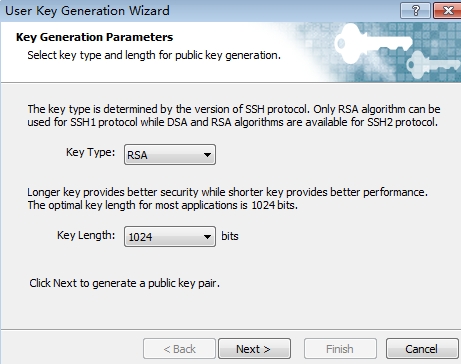
3.加密算法这里我选择RSA的加密,1024位
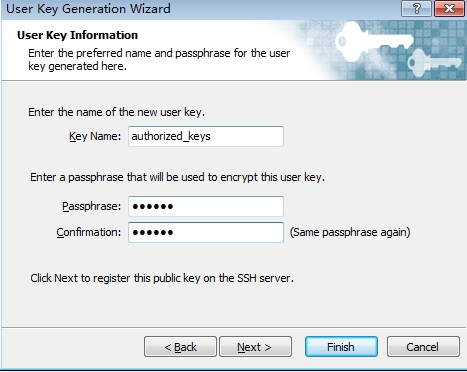
4.为了提高安全,添加密钥密码
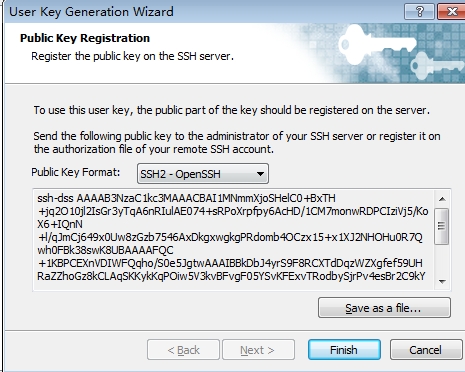
5.保存公钥,并把公钥上传到ssh服务器上,可以用winscp,ftp或者直接拖入已建立ssh的xshel界面里。
6.在linux服务器上添加用户dragon,并且分配密码
[root@localhost~]# useradd dragon
You have new mail in /var/spool/mail/root
[root@localhost ~]# passwd dragon
Changing password for user dragon.
New UNIX password:
BAD PASSWORD: it is based on a dictionaryword
Retype new UNIX password:
passwd: all authentication tokens updatedsuccessfully.
7.切换到dragon用户上,为了在dragon用户的根目录生成ssh,ssh连接到本地主机。
[root@localhost ~]# su dragon
[dragon@localhost ~]$ ssh localhost
The authenticity of host ‘localhost(127.0.0.1)‘ can‘t be established.
RSA key fingerprint isc5:08:8a:e3:b9:fb:44:f4:0b:e3:9f:c4:d7:e2:11:8a.
Are you sure you want to continueconnecting (yes/no)? yes
Warning: Permanently added ‘localhost‘(RSA) to the list of known hosts.
dragon@localhost‘s password:
[dragon@localhost ~]$ ls -a
. .. .bash_logout .bash_profile .bashrc .ssh
把把公钥放到dragon的.ssh里,并把权限改成644
[root@localhost ~]# mv authorized_keys/home/dragon/.ssh/
[root@localhost ~]# chmod 644/home/admin/.ssh/authorized_keys
8.切换回root修改ssh的配置文件,注意sshd_config是ssh服务器的配置文件。
把以下几项的注释去掉。
[root@localhost dragon]# vim/etc/ssh/sshd_config
RSAAuthentication yes //开启RSA加密
PubkeyAuthentication yes //开启公钥
AuthorizedKeysFile .ssh/authorized_keys //密钥的路径
PermitRootLogin no //禁止root登陆
PasswordAuthentication no //关闭密码验证
编辑完以后,重启sshd
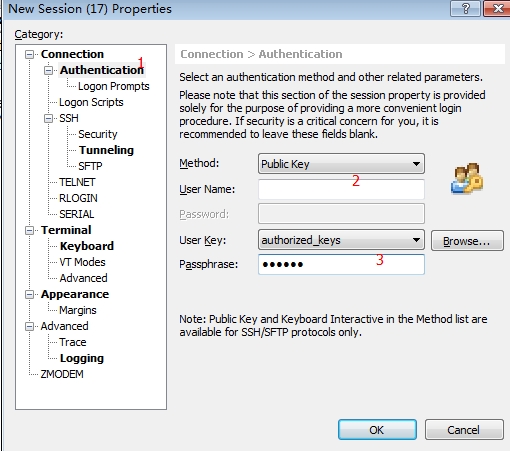
9.在window使用xshell连接服务器
用户dragon无需密码就能登录服务器
Last login: Fri Dec 5 20:29:09 2014 from 192.168.1.111
[dragon@localhost ~]$
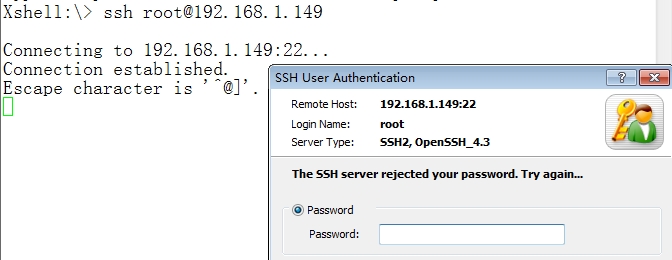
root登录的密码验证无法通过
linux与linux的ssh密钥验证
1.ssh-server添加用户admin,并分配密码。
[root@localhost ~]# useradd admin
[root@localhost ~]# passwd admin
Changing password for user admin.
New UNIX password:
BAD PASSWORD: it is based on a dictionaryword
Retype new UNIX password:
passwd: all a
uthentication tokens updated successfully.
2.切换到admin 在根目录ssh本地,生成.ssh
[admin@localhost ~]$ ssh localhost
The authenticity of host ‘localhost(127.0.0.1)‘ can‘t be established.
RSA key fingerprint isc5:08:8a:e3:b9:fb:44:f4:0b:e3:9f:c4:d7:e2:11:8a.
Are you sure you want to continueconnecting (yes/no)? yes
Warning: Permanently added ‘localhost‘(RSA) to the list of known hosts.
admin@localhost‘s password:
[admin@localhost ~]$ ls -a
. .. .bash_logout .bash_profile .bashrc .ssh
[admin@localhost ~]$
3.切换回root,修改配置文件/etc/sshd_config
RSAAuthentication yes //开启RSA加密
PubkeyAuthentication yes //开启公钥
AuthorizedKeysFile .ssh/authorized_keys //密钥的路径
PermitRootLogin no //禁止root登陆
PasswordAuthentication no //关闭密码验证
4.在客户机上生成公钥,并且scp上传到ssh-server上
[root$localhost ~]$ ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key(/home/admin/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in/home/admin/.ssh/id_rsa.
Your public key has been saved in/home/admin/.ssh/id_rsa.pub.
The key fingerprint is:
57:10:42:a9:87:d8:03:1d:f0:b0:f0:4d:5d:08:ea:33admin@localhost.localdomain
[root$localhost ~]$ ls .ssh
id_rsa id_rsa.pub known_hosts
[root$localhost .ssh]$ scp id_rsa.pubroot@192.168.1.149:/root/
The authenticity of host ‘192.168.24.169(192.168.24.169)‘ can‘t be established.
RSA key fingerprint is 01:77:02:41:8b:f3:86:3e:e9:58:b3:f2:91:34:91:90.
Are you sure you want to continueconnecting (yes/no)? yes
Warning: Permanently added ‘192.168.1.149‘(RSA) to the list of known hosts.
root@192.168.24.169‘s password:
id_rsa.pub 100% 409 0.4KB/s 00:00
5.在ssh-sever,把公钥存放在/home/admin/.ssh/,并且把权限改成644
[root@localhost ~]# mv id_rsa.pub/home/admin/.ssh/authorized_keys
[root@localhost ~]# chmod 644/home/admin/.ssh/authorized_keys
6.客户机通过密钥登陆ssh-seve,root被拒绝。
[root$localhost .ssh]$ ssh -ladmin192.168.1.149
Last login: Thu Mar 28 20:28:28 2013 fromlocalhost.localdomain
[admin@localhost ~]$
本文出自 “龙爱雪琪” 博客,谢绝转载!
ssh使用密钥验证
