首页 > 代码库 > firewald
firewald
firewald
一 iptables
1 )三张表五条链
1 filter:input:通过路由表之后目的地为本机
output:由本机产生,向外转发
forward:通过路由表之后,目的地不为本机
2 nat:prerouting:数据包进入路由表之前
postrouting:数据包进入路由表之后
input
output
3 mangle:prerouting,postrouting,input,output,forward
2 )配置
在配置iptables之前如果firewalld使开启的,要先stop和disables,不然会出现问题
iptables-L:列出指定表的策略
-n:不做解析
-A:添加策略
-t:指定表名称
-F:刷掉表中的所有策略,不用-t指定表名称时,默认为filter表
-p:网络协议
--dport:端口
-s:数据来源
-j:动作
-N:增加链
-E:改变链的名称
-X:删除链
-D:删除策略
-I:插入策略
-R:修改策略
-P:修改默认策略
ACCEPT:允许
REJECT:拒绝
DROP:丢弃
iptables -nL###没有指定表,默认为filter表,查看filter表的策略###
iptables -t filter###指定表名称为filter表###
iptables -F###刷掉法ilter表中的所有策略,当没有-t指定表名称时默认为filter表###
service iptables save###保存当前策略###
iptables -A INPUT -i lo -j ACCEPT###允许lo###
iptables -A INPUT -p tcp --dport 22 -j ACCEPT###允许访问22端口###
iptables -A INPUT -s 172.25.254.250 -j ACCEPT ###允许250主机访问本机所有端口###
iptables -A INPUT -j REJECT###拒绝所有主机的数据来源###
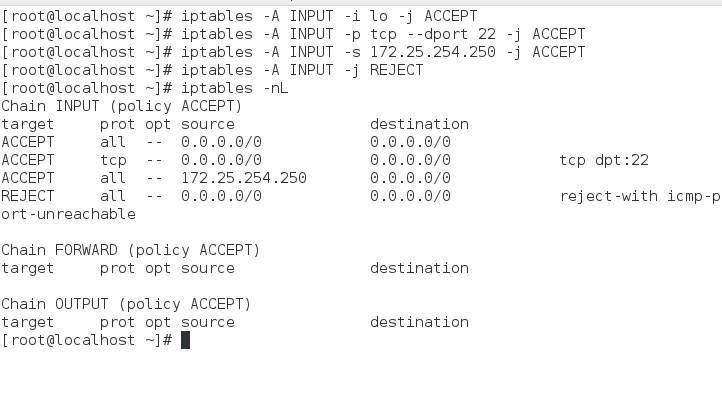
测试:
策略读取的顺序是逐条读取的,读到满足条件了,就不再往下读
查看78主机能否访问22端口
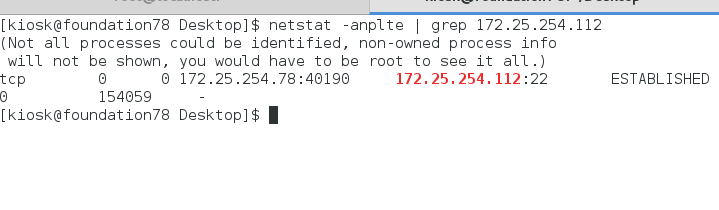
除了250主机以外的其他主机访问80端口
yum install links -y
links http://172.25.254.112

iptables -N redhat###增加链redhat##
iptables -E redhat westos###改变链名称###
iptables -X westos ###删除链westos###
iptables -D INPUT 2###删除第二条策略###
iptables -I INPUT -p tcp --dport 80 -j REJECT###插入策略,不指定时默认为插入第一条策略 ####
iptables -R INPUT 1 -p tcp --dport 80 -j ACCEPT ###修改策略###
iptables -P INPUT DROP###修改默认策略###
过程如下:
[root@desktop12 ~]# iptables -N redhat###增加链redhat##
[root@desktop12 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain redhat (0 references)
target prot opt source destination
[root@desktop12 ~]# iptables -E redhat westos###改变链名称###
[root@desktop12 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain westos (0 references)
target prot opt source destination
[root@desktop12 ~]# iptables -X westos ###删除链westos###
[root@desktop12 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop12 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
REJECT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop12 ~]# iptables -D INPUT 2###删除第二条策略###
[root@desktop12 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop12 ~]# iptables -I INPUT -p tcp --dport 80 -j REJECT###插入策略,不指定时默认为插入第一条策略 ####
[root@desktop12 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 reject-with icmp-port-unreachable
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop12 ~]# iptables -R INPUT 1 -p tcp --dport 80 -j ACCEPT ###修改策略###
[root@desktop12 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop12 ~]# iptables -P INPUT DROP###修改默认策略###
[root@desktop12 ~]# iptables -nL
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 172.25.254.12 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop12 ~]#
[root@desktop12 ~]# iptables -P INPUT ACCEPT
[root@desktop12 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 172.25.254.12 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop12 ~]#
iptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT ###添加策略,状态为RELATED,ESTABLISHED的允许连接###
iptables -A INPUT -i lo -m state --state NEW -j ACCEPT ###允许lo且状态为new###
iptables -A INPUT -p tcp --dport 22 -m state --state NEW -j ACCEPT ###允许连接22端口且状态为new###
iptables -A INPUT -p tcp --dport 80 -m state --state NEW -j ACCEPT ###允许连接80端口且状态为new###
iptables -A INPUT -p tcp --dport 443 -m state --state NEW -j ACCEPT ###允许连接443端口且状态为new###
iptables -A INPUT -p tcp --dport 53 -m state --state NEW -j ACCEPT ###允许连接53端口且状态为new###
过程如下:
[root@desktop12 ~]# iptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
[root@desktop12 ~]# iptables -A INPUT -i lo -m state --state NEW -j ACCEPT
[root@desktop12 ~]# iptables -A INPUT -p tcp --dport 22 -m state --state NEW -j ACCEPT
[root@desktop12 ~]# iptables -A INPUT -p tcp --dport 80 -m state --state NEW -j ACCEPT
[root@desktop12 ~]# iptables -A INPUT -p tcp --dport 443 -m state --state NEW -j ACCEPT
[root@desktop12 ~]# iptables -A INPUT -p tcp --dport 53 -m state --state NEW -j ACCEPT
[root@desktop12 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state NEW
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 state NEW
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 state NEW
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:443 state NEW
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:53 state NEW
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop12 ~]# vim /etc/sys
sysconfig/ sysctl.d/ system-release
sysctl.conf systemd/ system-release-cpe
[root@desktop12 ~]# vim /etc/sysconfig/iptables
[root@desktop12 ~]# service iptables save
iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ]
[root@desktop12 ~]#
sysctl -a | grep forward###查看forward的内核参数###
vim /etc/sysctl.conf
内容:
net.ipv4.ip_forward = 1###开启内核路由功能###
sysctl -p###立即生效###
iptables -t nat -A POSTROUTING -o eth1 -j SNAT --to-source172.25.254.100###添加策略,将ip通过eth1输出,并进行源地址转换,将其伪装成172.25.254.100###
iptables -t nat -A PREROUTING -i eth1 -j DNAT --to-dest 172.25.12.10###添加策略,将ip通过eth1输入,将其伪装成172.25.12.10
过程如下:
[root@localhost ~]# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@localhost ~]# iptables -t nat -A POSTROUTING -o eth1 -j SNAT --to-source 172.25.254.100
[root@localhost ~]# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 0.0.0.0/0 0.0.0.0/0 to:172.25.254.100
[root@localhost ~]# sysctl -a | grep forward
net.ipv4.conf.all.forwarding = 0
net.ipv4.conf.all.mc_forwarding = 0
net.ipv4.conf.default.forwarding = 0
net.ipv4.conf.default.mc_forwarding = 0
net.ipv4.conf.eth0.forwarding = 0
net.ipv4.conf.eth0.mc_forwarding = 0
net.ipv4.conf.eth1.forwarding = 0
net.ipv4.conf.eth1.mc_forwarding = 0
net.ipv4.conf.lo.forwarding = 0
net.ipv4.conf.lo.mc_forwarding = 0
net.ipv4.ip_forward = 0
net.ipv6.conf.all.forwarding = 0
net.ipv6.conf.all.mc_forwarding = 0
net.ipv6.conf.default.forwarding = 0
net.ipv6.conf.default.mc_forwarding = 0
net.ipv6.conf.eth0.forwarding = 0
net.ipv6.conf.eth0.mc_forwarding = 0
net.ipv6.conf.eth1.forwarding = 0
net.ipv6.conf.eth1.mc_forwarding = 0
net.ipv6.conf.lo.forwarding = 0
net.ipv6.conf.lo.mc_forwarding = 0
[root@localhost ~]# vim /etc/sysctl.conf
[root@localhost ~]# sysctl -p
sysctl: /etc/sysctl.conf(5): invalid syntax, continuing...
[root@localhost ~]# vim /etc/sysctl.conf
[root@localhost ~]# sysctl -p
net.ipv4.ip_forward = 1
[root@localhost ~]# iptables -t nat -A POSTROUTING -o eth1 -j SNAT --to-source 172.25.254.112
[root@localhost ~]# service iptables save
iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ]
[root@localhost ~]# iptables -t nat -A PREROUTING -i eth1 DNAT --to-dest 172.25.12.10
Bad argument `DNAT‘
Try `iptables -h‘ or ‘iptables --help‘ for more information.
[root@localhost ~]# iptables -t nat -A PREROUTING -i eth1 -j DNAT --to-dest 172.25.12.10
[root@localhost ~]# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT all -- 0.0.0.0/0 0.0.0.0/0 to:172.25.12.10
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 0.0.0.0/0 0.0.0.0/0 to:172.25.254.112
[root@localhost ~]# service iptables save
iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ]
[root@localhost ~]# iptables -t nat -A PREROUTING -i eth1 -j DNAT --to-dest 172.25.12.11
[root@localhost ~]# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT all -- 0.0.0.0/0 0.0.0.0/0 to:172.25.12.10
DNAT all -- 0.0.0.0/0 0.0.0.0/0 to:172.25.12.11
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 0.0.0.0/0 0.0.0.0/0 to:172.25.254.112
[root@localhost ~]#
firewald
