首页 > 代码库 > Configuring TLS Encryption Only for Cloudera Manager and Level 1
Configuring TLS Encryption Only for Cloudera Manager and Level 1
Configuring TLS Encryption Only for Cloudera Manager
on Cloudera Manager Server:
1. mkdir -p /opt/cloudera/security/{x509,jks,CAcerts}
2. generate a Java keystore and Certificate Signing Request (CSR) for the Cloudera Manager Server
keytool -genkeypair -alias cm5 -keyalg RSA -keystore /opt/cloudera/security/jks/cm5-keystore.jks -keysize 2048 -dname "CN=cm5.local,OU=IT,O=GKY,L=Shanghai,ST=Shanghai,C=CN" -storepass password -keypass password -validity 3650
3. Generate a certificate signing request for the host
keytool -certreq -alias cm5 -keystore /opt/cloudera/security/jks/cm5-keystore.jks -file /opt/cloudera/security/x509/cm5.csr -storepass password -keypass password
we use windows server 2012 CA to request a server certificate, save obtained server certificate to cm5cert.cer
4. Import the root CA certificate
download your Private CA root certificates to /opt/cloudera/security/CAcerts/rootca.cer
cp $JAVA_HOME/jre/lib/security/cacerts $JAVA_HOME/jre/lib/security/jssecacerts
keytool -import -alias RootCA -keystore $JAVA_HOME/jre/lib/security/jssecacerts -file /opt/cloudera/security/CAcerts/rootca.cer -storepass changeit
Once this step is complete, copy the jssecacerts file created to the same path on all cluster hosts.
5. import the Private CA certificates into your Java keystore file
keytool -import -trustcacerts -alias RootCA -keystore /opt/cloudera/security/jks/cm5-keystore.jks -file /opt/cloudera/security/CAcerts/rootca.cer -storepass password
6. cp cm5cert.cer /opt/cloudera/security/x509/cm5cert.pem
keytool -import -trustcacerts -alias cm5 -file /opt/cloudera/security/x509/cm5cert.pem -keystore /opt/cloudera/security/jks/cm5-keystore.jks -storepass password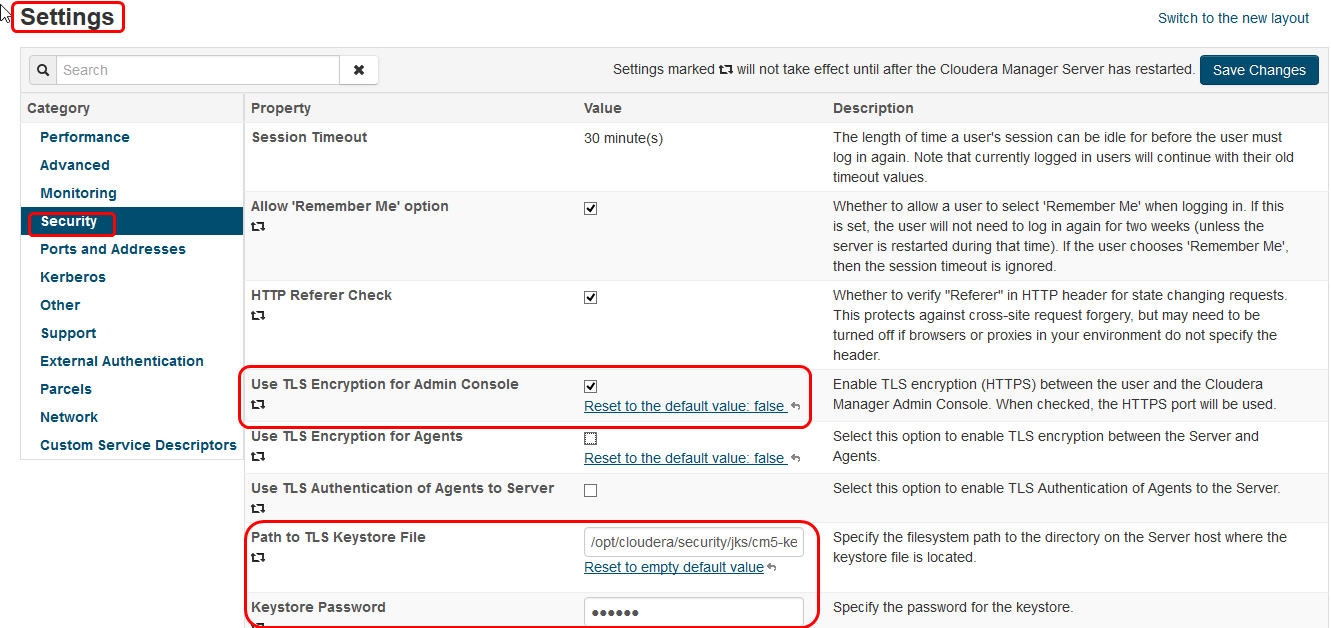
service cloudera-scm-server restart
http://cm5.local:7180 will redirect to https://cm5.local:7183
Level 1: Configuring TLS Encryption for Cloudera Manager Agents
1.on Cloudera Manager Server:
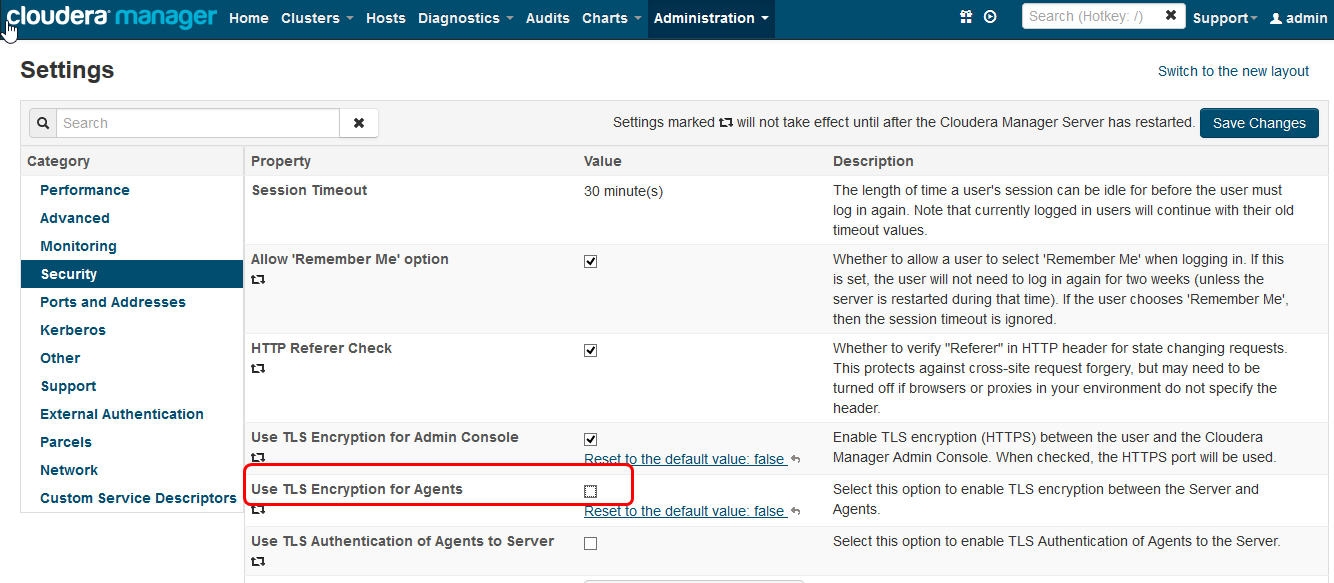
2. on all agent hosts:
vi /etc/cloudera-scm-agent/config.ini
use_tls=1
3. on Cloudera Manager Server:
service cloudera-scm-server restart
4. on all agent hosts:
service cloudera-scm-agent restart
5. In the Cloudera Manager Admin Console, open the Hosts page. If the Agents heartbeat successfully, TLS encryption is working properly.
本文出自 “Ilovecat(个人笔记)” 博客,请务必保留此出处http://hj192837.blog.51cto.com/655995/1580852
Configuring TLS Encryption Only for Cloudera Manager and Level 1
